This article is more than 1 year old
Ker-ching! NotPetya hackers cash out, demand 100 BTC for master decrypt key
Plus, bonus ransomware strain found lurking in software update
All the Bitcoins paid by victims of the NotPetya ransomware attack were withdrawn overnight.
Some paid the equivalent of $300 in Bitcoin even though there were no real means to recover their data. Just over 3.96 Bitcoins ($10,382) were drained from a wallet tied to NotPetya early on Wednesday morning, according to a Twitter bot monitoring the money store.
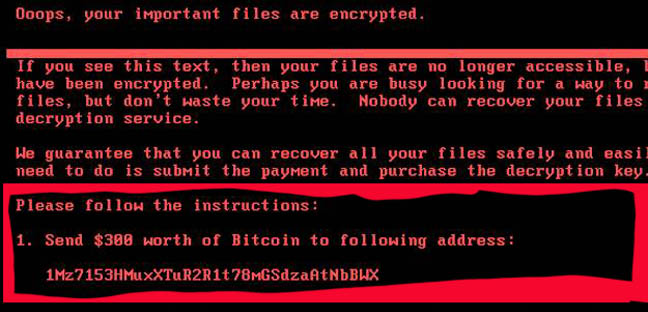
Hopeful Petya-smacked punters' contributions were drained from this Bitcoin wallet
Some of these funds were used to pay for a Pastebin Pro account on the dark web, which was subsequently used to post a fresh appeal for even more dosh. The malware's masterminds have demanded 100 Bitcoins – about a quarter of a million dollars – in exchange for a master private key that decrypts data scrambled by NotPetya. However, most victims, we imagine, have wiped and rebuilt their infected systems by now, meaning the key is useless to them.
As previously reported, NotPetya trashes compromised Microsoft Windows systems and acts more like a disk wiper than conventional ransomware. NotPetya spread to devastating effect last month using a variety of mechanisms. A poisoned update to a Ukrainian tax software program called MeDoc was the primary initial infection vector, according to security researchers.
An analysis by Kaspersky Lab reports that NotPetya was not the only ransomware pushed through MeDoc's hijacked software update channel. Unpacking that other nasty's code reveals that the project's name was "WannaCry" and that it pretends to be "made in China". These factors have prompted Kaspersky Lab researchers to dub the malware "FakeCry".
FakeCry used a ransomware screen resembling that used by NotPetya. To decrypt the files, the blackmailers asked for 0.1 Bitcoin, or around $260. Seven payments have been made into the fixed wallet used by FakeCry and most of the digital cash has reportedly been withdrawn.
The main NotPetya attack kicked off on June 27, and was centered in Ukraine, which accounted for four in five victims, according to security firm ESET. Banks, government agencies, newspapers, utilities, and Kiev's main airport were all affected. Other high-profile confirmed victims outside Ukraine included shipping giant Maersk, pharmaceutical giant Merck, and delivery firm FedEx.
The Security Service of Ukraine (SBU) is blaming Russian intelligence, claiming it was run by the same hackers behind the BlackEnergy attack against energy distribution utilities that resulted in brief blackouts back in December 2015. This remains unconfirmed. ®
