This article is more than 1 year old
Beijing police quench scum allegedly behind 'Fireball' fraudware
Eleven arrested over malicious browser plug-in that netted nearly US$12 million
Chinese police have moved on the developers of the Fireball adware that infected millions of computers earlier this year.
Fireball was described by Check Point in June after outbreaks in India, Mexico and Brazil. It bundled itself with legitimate software, and used browser plug-ins to boost its own advertisements.
At the time, Check Point named a Chinese digital marketing agency called Rafotech as author of Fireball.
Chinese outlets are now reporting eleven arrests by Beijing police, all of them Rafotech employees. Chongqing Morning News says three of those arrested were the company's president, technical director, and operations director.
In an English-language summary of the local reports, state-owned outlet "Sixth Tone" says the click-fraud netted 80 million yaun, nearly US$12 million.
Although reports of the arrests have emerged in the last few days, Sixth Tone says the arrests took place in June shortly after Check Point published its advisory.
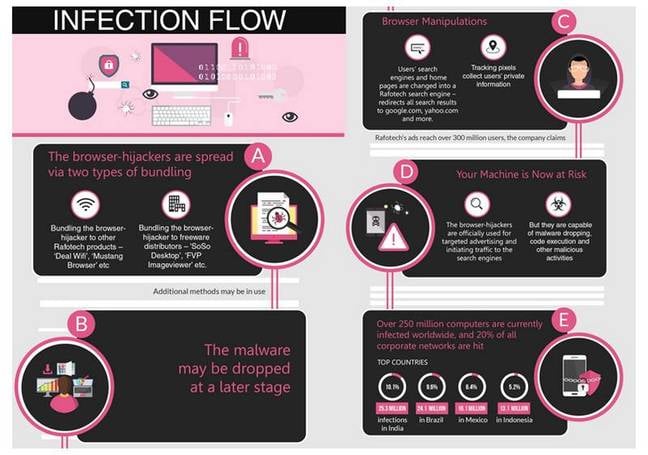
Fireball infection flow [source: Check Point blog post]. Click here to embiggen.
This report (after Google Translate) says police were tipped off by someone working under the pseudonym Zhang Ming, and that the Beijing Public Security Bureau Network Security Corps allowed Fireball to run for long enough that they could analyse its behaviour.
The perps have allegedly “admitted the facts” of their adware, which was first conceived around 2015, and that Rafotech was setup to develop and exploit the advertising fraud.
According to Beijing Youth Daily, Fireball was designed to avoid infecting Chinese computers, in an attempt to avoid breaking domestic laws. ®
