This article is more than 1 year old
Microsoft downplays alarm over Windows Defender 'flaw'
Says you'd hafta click through a *boatload* of warnings
Security researchers have uncovered what they believe is a vulnerability that allows malware to completely bypass Windows Defender. Microsoft dismissed the report as of "limited practical applicability" in practice (i.e. a low-risk threat).
The team at CyberArk Labs nonetheless claims the security shortcoming could impact tens of millions of devices running on Windows 10 and 8.1.
"In order to abuse Windows Defender," the researchers write, "an attacker would have to implement the SMB protocol and create a 'pseudo-server' that can differentiate Windows Defender's request from normal requests."
The group goes on to explain this creates a means to trick the system into scanning a different file than the one actually carrying malware. This means attackers could execute known malware behind the pretence of a legitimate file fed from an server message block (SMB) server, according to CyberArk Labs. A malicious file served in this way can be clicked on, and Windows Defender will scan a completely different and innocuous file – missing the malicious file. Despite this Windows will still load the real, malicious file. The technique therefore represents a means to circumvent Windows Defender, CyberArk said.
The researchers warn the flaw could be combined with phishing in targeted attacks. CyberArk goes on to suggest that other antivirus engines might also be vulnerable while admitting it hasn't actually tested this itself.
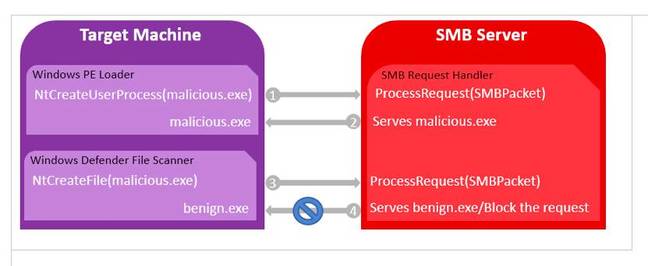
Fooling Windows Defender (Source: CyberArk Labs)
CyberArk writes that when it reported the "Illusion Gap" to Microsoft, the firm told it: "Based on your report, successful attack requires a user to run/trust content from an untrusted SMB share backed by a custom server that can change its behaviour depending on the access pattern. This doesn't seem to be a security issue but a feature request, which I have forwarded to the engineering group."
When El Reg asked Microsoft about this, it explained: "The technique described has limited practical applicability. To be successful, an attacker would first need to convince a user to give manual consent to execute an unknown binary from an untrusted remote location. The user would also need to click through additional warnings in order to grant the attacker Administrator privileges. Should the attacker successfully convince a user to carry out the manual steps mentioned, Windows Defender Antivirus and Windows Defender Advanced Threat Protection will detect further actions by the attacker." ®
