This article is more than 1 year old
Oz military megahack: When crappy defence contractor cybersecurity 'isn't uncommon', surely alarm bells ring?
30GB of data nicked in 'Alf's Mystery Happy Fun Time' attack
While Australia's federal government scrambles to hose down a hacking incident, it's important to ask why a defence contractor of any size could run a network so insecure it exposed default administrative interfaces to the Internet.
An Australian Signals Directorate (ASD) presentation to the Australian Information Security Association (AISA) conference yesterday detailed the hack.
I'm happy for the credit to remain with ZDNet's Stilgherrian for the story, since he was at the conference and I wasn't (the full horror is here).
Suffice to say that a medium-sized defence contractor was breached and gigabytes of aerospace data and commercial arrangements for military aircraft and naval vessels were delivered into the hands of the attackers. The ASD used it as a case study for the AISA conference yesterday.
The government has since said the information was commercial-in-confidence, but not classified.
This is not an isolated incident: in Australia, as elsewhere, attackers thwarted by a network's defences then seek out third-party contractors as an easier mark.
Horror movie in a PowerPoint slide
This slide from the presentation should frighten you:
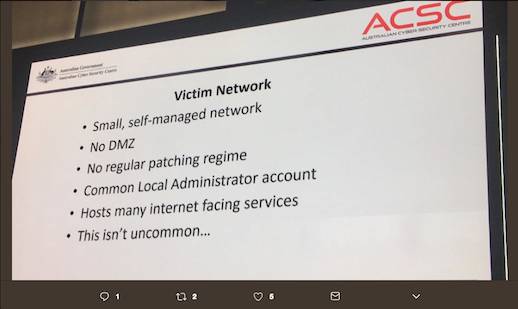
"This isn't uncommon" - Image credit Stilgherrian
What struck Vulture South was the long exposure window. The ASD slide sets it at a minimum four months – and adds "this isn't uncommon".
This suggests a problem in sub-contractor oversight – you can win a government contract without proving you have adequate network security.
Minister for Defence Industry Christopher Pyne seems to agree. This morning, he told Radio National's Breakfast programme that the government can't be held responsible for a contractor's lax security.
He added that the "upwards of 4,000" defence industry businesses in Australia need to take their cybersecurity seriously, and we agree.
The Register asked Nigel Phair, of the Centre for Internet Safety, about the policy or contractual requirements that apply to defence contractors.
"There's no stipulation [about required infosec measures], no ticklist of the essential eight [the ASD's don't-be-stupid list of protective measures – ed], or anything remotely sensible. That is a major issue," he said.
Things get worse the further away from the master contract you get: a sub-contractor can be so far removed from the master tender that things get very murky.
Phair said the government "needs to go through all these defence sub-contractors and sub-sub-contractors and audit them".
Yes, documents like the Defence Procurement Policy Manual (PDF) and the government's Protective Security Policy Manual exist. But try finding a suggested computer/network security framework in them.
Enforcement is also a gap. For example, there's no body randomly auditing contractors' internet-facing networks. Contractors have to promise to abide by non-disclosure agreements, but that's nothing more than a self-certification.
"It's like speeding: if you're not getting pulled over, you're free to claim you always drive within the speed limit," Phair said.
Defence isn't the only sector where very sensitive information is handled by sub-contractors of sub-contractors. The "Alf's Mystery Happy Fun Time" incident (an ASD wag named the attack after a television soap opera character from Home and Away) has to be seen in this context.
Australia's government has already made it clear that its vaunted facial recognition database will be accessible to the private sector. Yesterday it announced its intention to outsource Centrelink phone services to Serco, and one mission of its Digital Transformation Office is to present government as an API for others to use.
Governments hoping to reap financial, efficiency and national security dividends from outsourcing can no longer wash their hands of contractors' security. ®
