This article is more than 1 year old
Android ransomware DoubleLocker encrypts data and changes PINs
Nasty activated by home button unless device gets factory reset
Crooks have come up with a strain of Android ransomware that both encrypts user data and locks victims out of compromised devices by changing PINs.
DoubleLocker combines a cunning infection mechanism with two powerful tools for extorting money from its victims.
"Its payload can change the device's PIN, preventing the victim from accessing their device and encrypts the victim's data," said Lukáš Štefanko, the malware researcher at security firm ESET who discovered DoubleLocker. "Such a combination hasn't been seen yet in the Android ecosystem.
"DoubleLocker misuses Android accessibility services, which is a popular trick among cybercriminals."
The nasty is based on a banking trojan, which means that account-compromising functionality might easily be added.
The Android malware spreads in the very same way as its PC parent, as a fake Adobe Flash Player update that's pushed via compromised websites.
Once launched, the app requests activation of the malware's accessibility service, named "Google Play Service". After the malware obtains these accessibility permissions, it uses them to activate device administrator rights and set itself as the default Home application, in both cases without the user's consent.
"Setting itself as a default home app – a launcher – is a trick that improves the malware's persistence," Štefanko said. "Whenever the user clicks on the home button, the ransomware gets activated and the device gets locked again. Thanks to using the accessibility service, the user doesn't know that they launch malware by hitting Home."
DoubleLocker, once planted on a compromised device, creates two reasons for the victims to pay. First, it changes the device's PIN, effectively blocking the victim from using it. Second, DoubleLocker encrypts all files from the device's primary storage directory using the AES encryption algorithm.
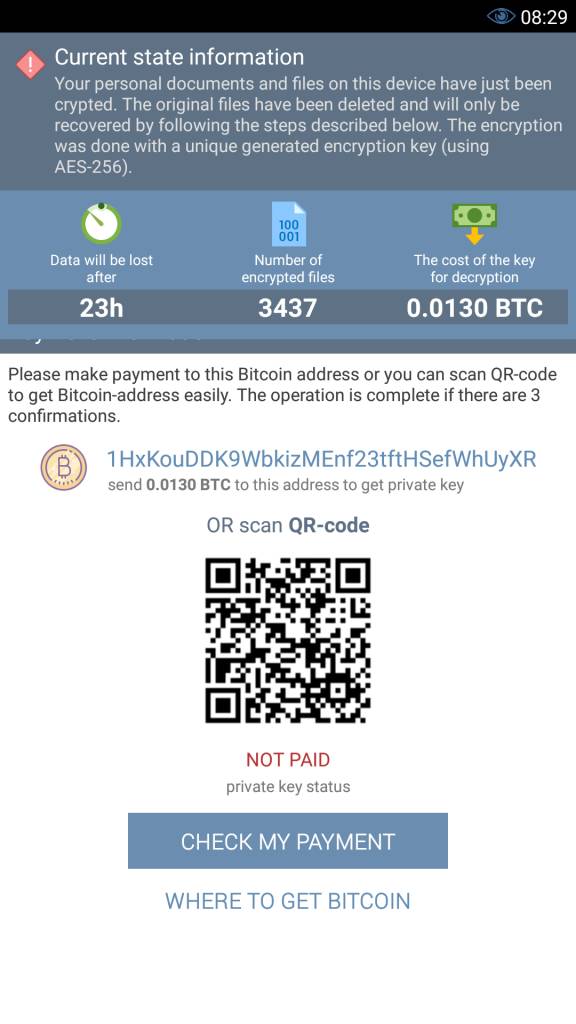
DoubleLocker ransom message [source: ESET blog post]
The ransom has been set at a relatively modest 0.0130 BTC (approximately $54). The only viable option to clean a non-rooted device of the DoubleLocker ransomware is via a factory reset. A way around the PIN lock on rooted devices is possible, if not exactly straightforward. Encrypted files can't be easily recovered. ®
