This article is more than 1 year old
Amazon's answer to all those leaky AWS S3 buckets: A dashboard warning light
Look out for that orange alert
Updated After watching customer after customer screw up their AWS S3 security and expose highly sensitive files publicly to the internet, Amazon has responded.
With a dashboard warning indicator. Simple, and hopefully effective.
For months now we have been reporting on researchers finding open S3 buckets packed full of confidential and very personal information, ready to be harvested by miscreants who stumble across the data stores. Accenture, Verizon, Viacom, Illinois voter information and military information has all been found inadvertently left open to everyone online due to IT bods misconfiguring their S3 silos.
A few weeks ago, we asked Amazon for advice to give to Reg readers – literally millions of people working in the technology industry – on how to make sure their AWS-hosted systems are locked down and secured from prying eyes. The biz's spokespeople um'd and ah'd a bit, it all went very quiet, and now we're presented with a solution.
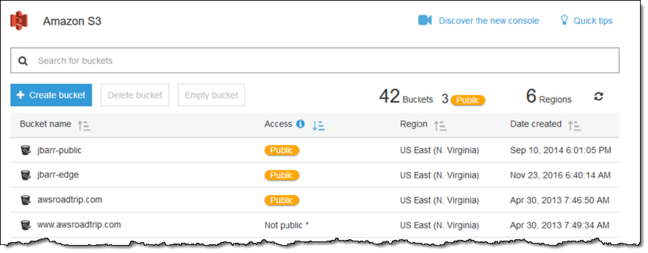
In a blog post today, Jeff Barr, chief evangelist for AWS, announced five new security features for the cloud service. In particular, Amazon is addressing the open S3 bucket issue with a very high-tech solution – a yellow-orange button.
Sarcasm aside, frankly anything would have been better than the current situation, and there is also a warning bar that pops up when configuring permissions as an additional reminder to not basically blab your project's secrets. And there are some genuinely welcome additions on the security side for S3 users announced today that could also prove very helpful indeed.
For a start, users can activate a bucket encryption configuration that automatically encrypts every file dropped into it without exceptions. Subscribers can use a key manager to control access to the data, and select the crypto algorithm to use, such as AES-256, via a PUT request.
To lock down multi-region accounts, Amazon is extending the use of Access Control Lists for bucket contents. Admins can set access permissions for files, and when files are replicated to another region, these settings will be automatically transferred with them. If peeps use the AWS Key Management Service, encrypted files can be duplicated across regions, too, and still be accessible via the key service. As an extra safeguard there's also a new inventory reporting screen so that admins can rapidly see what's locked down and what isn't.
All in all, from what we can tell, these are going to be very welcome additions to AWS and, as an added bonus, Amazon isn’t charging for them. Now we wait and see how humans can forget to use them, but it will hopefully lead to fewer stories of open S3 buckets spilling secrets. ®
Updated to add
Amazon's updated security systems are helpful, but not enough thanks to one crucial flaw in the plan, Chris Vickery of security shop Upguard told The Register.
"It all comes down to people," the hunter of exposed S3 buckets explained. "If you give people the option to create an insecure storage site then there's always going to be someone who does it – no matter how secure they can make it if they chose."
When asked, Vickery said that if he were in charge at Amazon he'd create a secure storage platform that users couldn't override or misconfigure. It would never happen because it would be rather restricted and staggeringly less profitable, he pointed out.
The new tools also don't appear to have that great an effect so far. Vickery said he had been scanning open S3 buckets this morning and it doesn’t appear the security additions are retroactive. Even if S3 accounts eventually get locked down, there are other fish to fry.
"I started off doing this on MongoDB databases before moving on to Amazon," he said. "I don’t see an end in sight; there is always going to be something to look for."
PS: Amazon is switching from the Xen hypervisor to its own custom KVM software.