This article is more than 1 year old
Mirai, Mirai, pwn them all, who's the greatest botnet on the whole?
Variants on zombie horde that took down Dyn still at large
The Mirai botnet is alive and kicking more than a year after its involvement in a DDoS attack that left many of the world's biggest websites unreachable.
DNS provider Dyn reckons about 100,000 Mirai-infected gadgets knocked it out back in October 2016. A study by security ratings firm SecurityScorecard, out Tuesday, found that even a year after its initial release, Mirai botnet infections are still widespread.
From July to September 2017, SecurityScorecard identified 34,062 IPv4 addresses on the public internet that showed symptoms expected from an embedded device infected with the Mirai IoT malware. This contrasts with 184,258 IPv4 addresses of IoT devices infected with Mirai IoT malware from August 1, 2016, to July 31, 2017.
Even though the botnet is smaller and more fragmented, it still poses a threat to internet hygiene.
Other security experts back this assessment. The decline in numbers of the Mirai zombie horde may have nothing to do with improved IoT security, such as users patching the DVR devices and the like that are most susceptible to infection.
Ken Munro, of UK security consultancy Pen Test Partners, said: "We believe the main reason that the botnets are small is that Mirai is not persistent. The infection does not survive a reboot. Mirai attacks XiongMai-based DVRs, which are pretty unstable – indeed, it's trivial to reboot them remotely, unauthenticated.
"As a result, no single botnet herder can create a single large botnet – the DVRs reboot randomly and there's then a race to pwn then again."
Other more recent IoT botnets – most notably Reaper – represent a worse risk to security, according to Munro.
The attack on Dyn was preceded by one on infosec sleuth Brian Krebs' website and followed by DDoS attacks using Mirai variants on the routers of Deutsche Telekom and TalkTalk. All of this malfeasance took place last year. Quite why we've not seen a continuation of high-profile DDoS attacks that use IoT devices as a platform is something of a head-scratcher, not least because the potential for harm is undiminished.
For example, last month security researchers Troy Mursch and Dr Neal Krawetz uncovered a Mirai-like botnet made up of EnGenius routers. Mursch told El Reg that he's seen 90,000 drones in the network since February.
Mirai source code leaked in early October 2016, three weeks or so before the Dyn DDoS spectacular. This has opened up the door to copycat botnet cultivation.
What's the sitch?
SecurityScorecard's Mirai sitrep provides a contemporary analysis of the devices infected with the IoT malware.
The education sector was the industry most affected by Mirai variants during Q3 of 2017, ahead of energy, manufacturing, entertainment, and financial services, according to figures from SecurityScorecard.
Mirai spread by industry sector pie chart [source: SecurityScorecard]
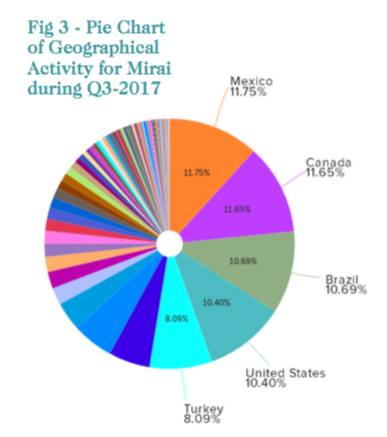
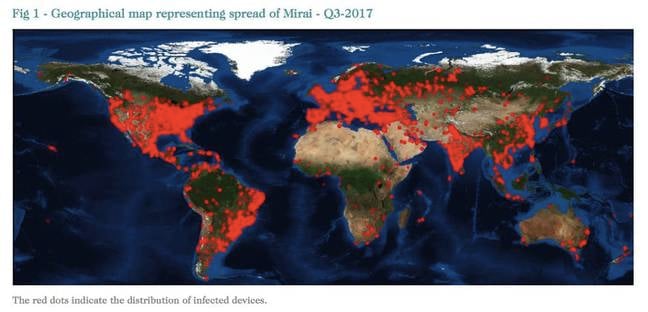
The most affected country for Mirai activity in Q3 of 2017 is Mexico, ahead of China, the US, Brazil and Turkey.
Geographical map of spread of the Mirai botnet
The prevalence of Mirai infections in Mexico is likely a byproduct of efforts to roll out IoT systems, such as the recent availability of a regional dedicated communications service specifically geared towards the Internet of Things. ®
