This article is more than 1 year old
Credential-stuffing defence tech aims to defuse password leaks
Blackfish detects stolen logins as they are used by cybercrims
A system that aims to identify stolen passwords before breaches are reported or even detected was launched on Tuesday.
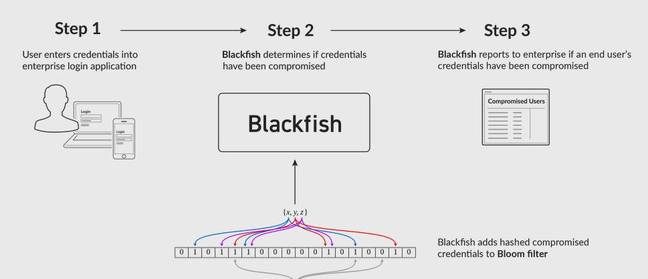
Shape Security's Blackfish credential defence system is designed to detect the use of stolen usernames and passwords by criminals and in real time.
The technology is a mechanism for organisations to identify the abuse of stolen passwords and attempts to hijack accounts long before these same purloined credentials show up for sale on the dark web.
Cybercrooks regularly automate the process of testing stolen or leaked passwords on third-party websites.
For example, customers of online takeaway firm Deliveroo found their accounts hijacked and charged for food they never ordered because of a credential-stuffing attack. In another attack using the same method, passwords and email addresses from previous breaches were abused to gain access to 26,000 online UK National Lottery accounts. Groupon blamed fraudulent purchases from some UK customers' accounts on password leaks from other sites.
Credential stuffing only works because many users still use the same login details on multiple sites. This is a serious security risk that's only getting worse as the volume of data breaches rises.
Shape Security's network data shows that in many industries, such as retail, more than 90 per cent of all login attempts to websites often come from credential-stuffing attacks instead of genuine users.
Shape Security's customer base includes three of the top-four banks, four of the top-five airlines, two of the top-five hotel chains, and two of the top-five US government agencies. Crowdsourcing alerts about brute-force credential-stuffing attacks among its customers makes for an effective early warning system, the firm claims.
CTO and former Google clickfraud czar Shuman Ghosemajumder told El Reg: "Cybercriminal organizations are businesses, and they need an ROI, so it just doesn't make sense for them to go after smaller websites with credential-stuffing campaigns. Over the last five years, Shape has created and deployed technology to protect the login systems of the major banks, airlines, retailers, and other industries where cybercriminals first use stolen credentials to take over accounts.
"So in this case there isn't much of a 'long tail' associated with the attack data, since cybercriminal activity is concentrated in the high end of the market."
Facebook, Twitter and other companies have been researching the dark web for several years, acquiring lists of stolen credentials to protect their users. "This can be helpful but its utility is limited," said Ghosemajumder. "Darknet-sourced lists of stolen credentials tend to have much less value compared to credentials which have been recently stolen, which sophisticated cybercriminals first use against leading consumer sites, such as those that Shape protects."
Shape's credential defence technology ultimately aims to end credential-stuffing attacks by making stolen data worthless to cybercriminals. But initial reaction from security experts has been mixed.
Per Thorsheim, founder of PasswordsCon, commented: "They want to collect passwords used in the wild against sites and services, then provide them to customers who can find and invalidate (change) accounts using those passwords. Interesting idea, but skeptical to both security and user experience. This is an online service. What happens if they are not online?"
Troy Hunt, the security researcher behind the haveibeenpwned breach notification service, said it was hard to comment on the utility of the service from Shape's marketing materials alone.
Sarah Squire, co-author of the NIST Digital Identity Guidelines, was more upbeat: "In June, the National Institute of Standards and Technology issued the recommendation that all companies check their users' credentials against breached password corpuses. Shape is going one step further by enabling companies to cross-reference with a breach corpus that is actively exploited and not dependent on companies self-disclosing breaches in a timely manner." ®