This article is more than 1 year old
Microsoft says Win 8/10's weak randomisation is 'working as intended'
This bug is a feature in 11 out of 12 scenarios
Microsoft has rebutted analysis that suggested its Address Space Layout Randomisation (ASLR) technology could be exploited.
Redmond's response, posted here, was that ASLR is working as intended, and that the lack of randomisation discovered by Will Dormann - with assistance from Matt Miller of Microsoft - was a feature, not a bug.
“In short, ASLR is working as intended and the configuration issue described by CERT/CC only affects applications where the EXE does not already opt-in to ASLR. The configuration issue is not a vulnerability, does not create additional risk, and does not weaken the existing security posture of applications”, the post (attributed to the Microsoft Secure Windows Initiative) stated.
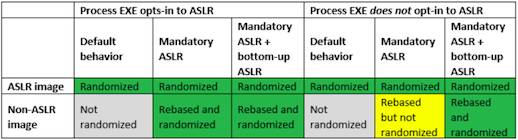
The post said Dormann's discovery only applied for the case coloured yellow in the table above, adding: “the entropy of images rebased by mandatory ASLR is inherently reliant on bottom-up randomisation being enabled for the process”.
Because bottom-up randomisation isn't automatically enabled if the EXE has not opted into ASLR, the post said, the developer has to explicitly do so “for entropy to be applied to images that are rebased by mandatory ASLR. In practice, this issue only affects scenarios where an administrator is intentionally attempting to enable mandatory ASLR for a process that would otherwise not fully benefit from ASLR.”
So, no bug, no vuln, right?
Not quite, the post continued:
“CERT/CC did identify an issue with the configuration interface of Windows Defender Exploit Guard (WDEG) that currently prevents system-wide enablement of bottom-up randomisation … Similarly, EMET does not support enabling bottom-up randomisation system-wide and therefore cannot directly configure this setting.”
Vulture South checked this with Dormann, who agreed:
The system-wide mandatory ASLR design starting with Windows 8 is surely a feature.
— Will Dormann (@wdormann) November 21, 2017
The fact that neither EMET nor Windows Defender Exploit Guard took this design change into account sounds like a bug to me.https://t.co/d0KIJiin97
Until fixed, set registry manually if you want it pic.twitter.com/eXftGhWcrZ
Microsoft agreed with the workarounds Dormann suggested in the CERT/CC announcement: either edit a registry value, or force it on a program-specific basis. ®
