This article is more than 1 year old
Someone is touting a mobile, PC spyware platform called Dark Caracal to governments
Hundreds of gigabytes already slurped, say EFF and Lookout
An investigation by the Electronic Frontier Foundation and security biz Lookout has uncovered Dark Caracal, a surveillance-toolkit-for-hire that has been used to suck huge amounts of data from Android mobiles and Windows desktop PCs around the world.
Dark Caracal [PDF] appears to be controlled from the Lebanon General Directorate of General Security in Beirut – an intelligence agency – and has slurped hundreds of gigabytes of information from devices. It shares its backend infrastructure with another state-sponsored surveillance campaign, Operation Manul, which the EFF claims was operated by the Kazakhstan government last year.
Crucially, it appears someone is renting out the Dark Caracal spyware platform to nation-state snoops.
"This is definitely one group using the same infrastructure," Eva Galperin, the EFF's director of cybersecurity, told The Register on Wednesday. "We think there's a third party selling this to governments."
Dark Caracal has, we're told, been used to siphon off information from thousands of targets in over 21 countries – from private documents, call records, audio recordings, and text messages to contact information, and photos from military, government, and business targets, as well as activists and journalists.
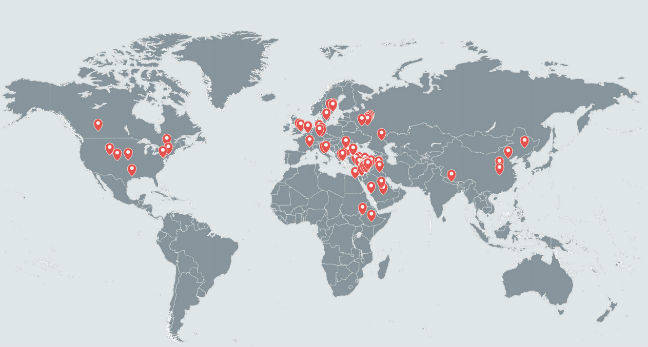
Dark Caracal has an impressive geographical reach ... Each dot marks the general location of an infected victim
After the EFF published its dossier on the Operation Manul cyber-snooping program in 2016, Lookout went looking through its database of collected malware samples to hunt down the spyware responsible. Lookout found the code nasty, a custom-made piece of Android evilware dubbed Pallas, which appears to be a component of the Dark Caracal toolkit.
In other words, Pallas is used to hijack targets' smartphones, and is distributed and controlled via the Dark Caracal platform rented out to governments.
The primary way to pick up Pallas on your gadget is by installing infected applications – such as WhatsApp and Signal ripoffs – from non-official software souks. Pallas doesn't exploit zero-days to take over a device, but instead relies on users being tricked into installing booby-trapped apps, and granting the malicious software a large variety of permissions. Once in place, it can thus surreptitiously record audio from the phone's microphone, reveal the gizmo's location to snoops, and leak all the data the handset contains to its masters.
In addition, the Dark Caracal platform offers another surveillance tool: a previously unseen sample of FinFisher, the spyware package sold to governments to surveil citizens. It's not known if this was legitimately purchased, or a demo version that was adapted.
On the desktop side, Dark Caracal provides a Delphi-coded Bandook trojan, previously identified in Operation Manul, that commandeers Windows systems. Essentially, marks are tricked into installing and running infected programs signed with a legitimate security certificate. Once up and running, the software nasty downloads more malware from command-and-control servers. The code pest can also be stashed in Microsoft Word documents, and executed using macros – so beware, Office admins.
The EFF and Lookout are trying to find out who exactly is running and using the Dark Caracal network. An update is expected in the summer, once attribution can be made with some certainty. ®
