This article is more than 1 year old
Another week, another Cisco-security-kit-needs-a-patch story
Probing last week's ASA and Firepower flaws found another DDOS to deter
Cisco's again asked owners of Adaptive Security Appliances or Firepower Threat Defense Software to patch, after it turned up a new DDOS problem that last patches didn't address.
Owners of such kit were in patch-fast mode last week after Switchzilla revealed a “crafted XML attack” that exposed webvpn's interface to the 'net, permitting denial of service or remote code execution.
Now Cisco's revealed that its probes into the problems revealed a further DOS vector.
Omar Santos, a principal engineer in Cisco's Product Security Incident Response Team, wrote that working with NCC Group's Cedric Halbronn (who made the original bug report), it was “found that the original list of fixed releases published in the security advisory were later found to be vulnerable to additional denial of service conditions”.
Santos added quick diagnostics for anybody wanting to know if their configuration is vulnerable: the key port will show up in response to the command show asp table socket | grep SSL|DTLS:
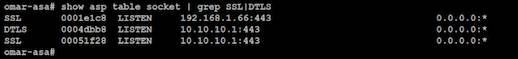
The presence of an SSL or DTLS listen socket on any TCP port indicates vulnerability.
Since IKEv2 configurations are also vulnerable, checking that as shown below also seems prudent.
![]()
![]()
The new patch is available at Cisco's updated advisory.
If you want complete understanding of the bug, NCC Group has put together a 120-page presentation [PDF] for Recon Brussels. ®
