This article is more than 1 year old
Oh, Bucket! AWS in S3 status-checking tool free-for-all
'Your data is waiting for the internet to download it' warning lights are now free
Amazon Web Services has signalled it's still worried about poorly configured buckets in its Simple Storage Service (S3) by making one of the tools to manage them free.
AWS suffered last year after a rash of data leaks caused by customers who had improperly configured their S3 storage.
It's an easy mistake to make because the routine for building a new bucket offers the chance to set policies from an existing bucket. Forget the settings on an old one and - pow - your stuff could all be online. Or you could fat-finger the "Manage Public Permissions" dialog and choose the unsafe option.
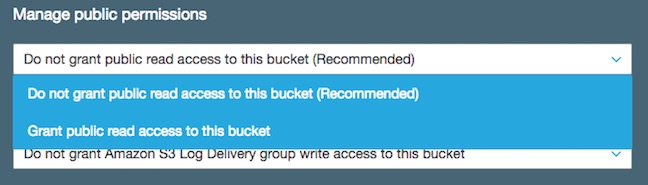
Whatever the reason for buckets being left naked and alone on the internet, AWS was embarrassed by association with careless users and last year gave the world a tool that flashed orange alerts when insecure buckets polluted users' AWS fleets.
Now the company has decided the version of that tool included in its Trusted Advisor service needs to be free.
"Previously available only to Business and Enterprise support customers, this check identifies S3 buckets that are publicly accessible due to ACLs or policies that allow read/write access for any user," the cloudy colossus said.
Given that the original tool wasn't much more than a yellow light on a management console, making it more widely available for free may not stem the tide of badly-built buckets. But at least AWS can say it's trying to help. ®
