This article is more than 1 year old
Hackers create 'ghost' traffic jam to confound smart traffic systems
Fake messages from one car enough to clog a whole intersection
Video How many “adversarial vehicles” do you need to befuddle smart traffic lights? Just one, according to research published in late February.
Five researchers from the University of Michigan attacked the traffic control system the US Department of Transportation has been using for trials since 2016.
Called I-SIG (Intelligent Traffic Signal System), the system feeds real-time vehicle trajectory data into an algorithm that controls the duration and sequence of traffic lights (its real-world deployments are at intersections in Palo Alto, California, and Anthem in Arizona), recording a 26.6 per cent reduction in vehicle delays.
Unless, of course, the system's getting fake data, the researchers wrote in this paper (PDF). In that case, a half-minute jaunt could be dragged out to a stunning 14 minutes.
“The only attack requirement in our study is that attackers can compromise the vehicle-side devices on their own vehicles or other people’s vehicles, and send malicious CV [connected vehicle] messages to the I-SIG system to influence the traffic control decisions”, they wrote.
The group set two other constraints around their attack: they did not “crack” the messaging system, instead generating their fake messages from a real vehicle. This left the I-SIG's Security and Credential Management System (SCMS) intact. They also assumed “only one attack vehicle exists at an intersection”.
And, as the image below shows, the attack can work even if the “adversarial vehicle” is parked nearby the target intersection.
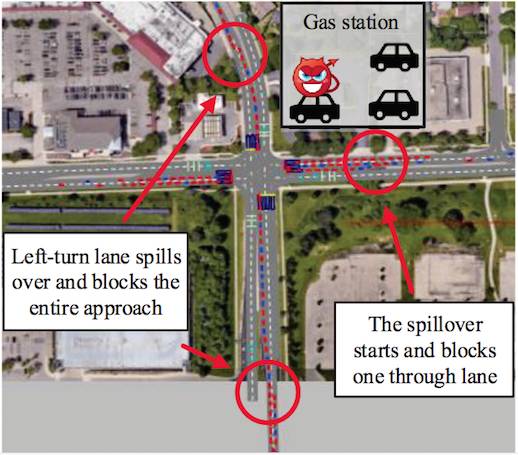
One attack vehicle parked near an intersection can cause chaos
The attack manipulates the mechanism I-SIG uses to manage queues, by spoofing the attack vehicle's predicted arrival time and the requested phase of the traffic lights (I-SIG lets vehicles request a green light for their arrival, and decides whether or not to grant it based on the queue it's created of all the incoming requests).
“The attacker can change the speed and location in its BSM [Basic Safety Message – El Reg] message to set the arrival time and the requested phase of her choice and thus increase the corresponding arrival table element by one”, the paper said.
The attack, they claimed, has a 94 per cent success rate, and on average, would increase delays by 38.2 per cent.
The best defence against these and other attacks, the researchers say, is a combination of more robust algorithms, better performance in the roadside units that give the system its realtime feedback, and better validation of vehicle-originated messages. ®
