This article is more than 1 year old
Researcher found Homebrew GitHub token hidden in plain sight
'Kid, take a nap, I have a project to save'
The popular Homebrew macOS package installer has moved to plug a serious vulnerability – it accidentally left a GitHub token visible to the public. Luckily, a team member on paternity leave had a moment while their child napped to fix it.
Homebrew does for macOS what apt-get does for Debian: it's a handy installer for stuff that doesn't come as a convenient App Store image.
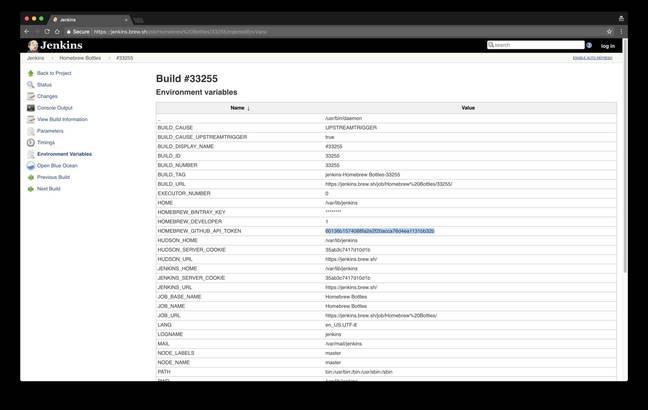
As the project explains in its disclosure: "A GitHub personal access token with recently elevated scopes was leaked from Homebrew's Jenkins that gave [the researcher] access to git push on Homebrew/brew and Homebrew/homebrew-core."
Eric Holmes, who discovered the problem, wrote that he was able to get into Homebrew in 30 minutes.
The credential in question was exposed because "builds in the 'Homebrew Bottles' project were making authenticated pushes to the BrewTestBot/homebrew-core repo", and the credentials for those pushes (a GitHub API token) were stored in Homebrew's Jenkins.
"If I can gain access to commit in 30 minutes, what could a nation state with dedicated resources achieve against a team of 17 volunteers?" Holmes asked.
In this case, that hasn't happened, according to Homebrew. GitHub support "verified the relevant token had not been used to perform any pushes to Homebrew/brew or Homebrew/homebrew-core during the period of elevated scopes".
That, Homebrew said, demonstrated that none of its packages had been compromised, and users need not worry.
It also observed that it's hard for a small group of volunteers to respond quickly to issues. "The Homebrew maintainer who resolved the above issues was on paternity leave from work and the primary carer for their child and had to reach a quick resolution while their child had a nap."
Homebrew said it's been using 2FA and third-party application restrictions on its GitHub for "several years", has now "enabled branch protection and required reviews on additional repositories", and asked maintainers to review their access tokens and disable SMS fallback for 2FA. The group said its leadership group voted not to add GPG signing to Homebrew/homebrew-core. ®