This article is more than 1 year old
Drama as boffins claim to reach the Holy Grail of superconductivity
But odd results and email impersonation raise eyebrows
A pair of physicists have claimed to reach the holy grail in physics: room temperature superconductivity.
Unsurprisingly, the results have raised several eyebrows and the fear of another cold fusion fiasco. It has also led to a series of strange events involving the impersonation of a famous physicist using an encrypted email address.
But first, let’s go back to superconductivity. Superconductive magnets are used to generate powerful magnetic fields that drive everything from maglev trains to high speeds, power fusion reactors, and for medical imaging.
It’s a weird phenomenon that emerges when a substance is cooled below a certain temperature, giving it zero electrical resistance. The critical temperature varies for different materials, but it generally requires cryogenic fluids like liquid helium to force materials into their superconductive state, making superconductivity expensive and fiddly.
Physicists have been steadily increasing the temperature for superconductivity by employing tricks like increasing the pressure exerted on materials. The highest confirmed temperature yet is about 203 kelvin or -70 degrees Celsius when hydrogen sulfide is put under a pressure of about 150 gigapascals - over a million times more than the pressure of the atmosphere.
The lure of perfect conductivity and 100 per cent energy efficiency at room temperature would revolutionize everything from power grids to computers. So when a paper floating around on arXiv [PDF] promised superconductivity “at ambient temperature and pressure conditions” in silver and gold particles, people were quick to notice.
Dev Kumar Thapa and Anshu Pandey, researchers at the Indian Institute of Science, Bangalore, claim that silver particles embedded in samples of gold can become superconductive at 236 kelvin or -37.15 degrees Celsius. Thapa is apparently a student that is on the verge of, or has recently completed, his PhD thesis, and Pandey is an associate professor.
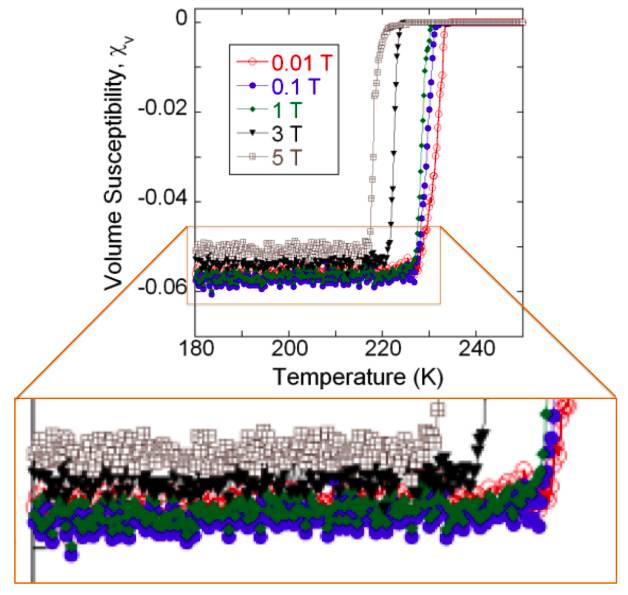
Brian Skinner, a postdoctoral researcher in theoretical condensed matter physics at the Massachusetts Institute of Technology, studied the paper. At first, he thought that the results looked consistent and was pretty convincing until he zoomed into one of the graphs.
Bring on the noise
The graph plots a material’s magnetic susceptibility - the degree at which the material becomes magnetized after a magnetic field is applied - at a given temperature. The jump up in magnetic susceptibility is when the material is approaching its critical temperature to become superconductive.
Skinner noticed that the pattern of green and blue data plots are pretty much exact copies of each other only shifted down by a constant amount. He consulted other physicists at MIT and elsewhere to see if they had encountered anything like it in their experiments. But all of them were very baffled by it and could think of no obvious explanation for it.
He then wrote a short paper on arXiv to discuss the results of the claims. “This unusual feature of repeated noise in the magnetic susceptibility has, to my knowledge, no precedent in the superconducting literature, and no obvious theoretical explanation,” he wrote.
Pratap Raychaudhuri, a professor focused on superconductivity at the Tata Institute of Fundamental Research in Mumbai, pointed out that mysterious noise patterns had been observed. They were spotted in the Schön scandal, when German physicist Jan Hendrik Schön reported a series of scientific breakthroughs that were later exposed as lies.
“By definition noise patterns are random and cannot reproduce. One of the biggest fraud in the history of physics, the Hendrik Schon scandal, was unearthed precisely by looking at the noise pattern that matches exactly in independent measurements. The Skinner report thus immediately raised a red flag of possible academic misconduct: carelessness or outright fraud,” Raychaudhuri said in a Facebook post.
It doesn’t look too good for Thapa and Pandey so far. But the story gets worse; here’s where it gets weird.
Fake email conversations
Days after his critical comments, Raychaudhuri gets an email from Tiruppattur Venkatachalamurti Ramakrishnan, also known as T. V. Ramakrishnan, a highly esteemed Indian theoretical physicist.
He asks Raychaudhuri not to criticize the authors on social media and to be patient. It also includes a string of forwarded emails that appears to be a conversation between Ramakrishnan and Pandey.
Raychaudhuri fired off a stern response, and later gets a strange call from Ramakrishnan. Ramakrishnan said he saw the email thread, but said he had never sent those emails himself. “He did not have the slightest clue on who could have done this. I felt terribly embarrassed for the unkind words that I wrote and apologized,” Raychaudhuri told El Reg.
It turns out that the fake emails had been sent from a protonmail server, an encrypted email service based in Switzerland. The email account appears to have been shut down since. We asked the authors a series of questions, including if they had created the protonmail account and sent those emails to Raychaudhuri.
Anshu did not answer those questions, but told us: “We are having our results validated by independent experts in the respective research fields. This process takes time. Without validation, the synthesis and device fabrication details are speculative and will add to further confusion. We will announce the results of validation in the appropriate forum as soon as possible.”
So it looks like they aren’t giving up quite yet. But scientists aren’t convinced. “The experimental claim here is so big that I think it would take a lot of evidence to convince me and the larger physics community that there really is a room temperature superconductor. We would need to see similar results replicated by at least one other independent group, and more experimental details and more data posted,” Skinner told The Register.
Raychaudhuri agreed and said Thapa and Pandey needed to understand that their scientific reputation is at stake.
“Let them give up their greed of earning a billion dollar in patent and be more open about their data and sample. Let their colleagues convince them that it is in their best interest to do so instead of hiding behind technicalities.”
“Finally, I love the fact that we are all living in interesting times. Let us argue, let us fight, let us raise a stink and let us clear it ourselves! Let us make the best of the situation. Whether Thapa and Pandey win or not, let science win. Silence is not an option.” ®