This article is more than 1 year old
Oslo clever clogs craft code to scan di mavens and snare dodgy staff
There's Norway you can escape detection, thanks to computers, software, and skills
Researchers from the University of Oslo in Norway have developed a system that tries to combat rogue employees and inside jobs – by combining cyber and real-world security knowhow.
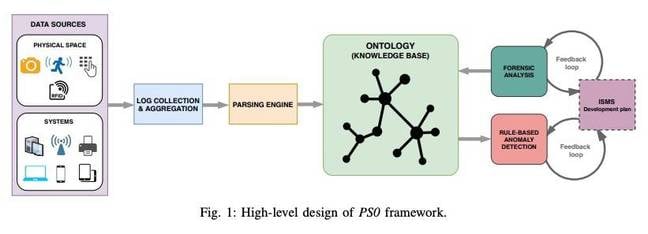
Known as PS0, the framework [PDF] combines traditional PC and network security systems with input from physical sensors and other surveillance hardware such as cameras and ID badges, eventually combining all of it into a single database that could be queried by administrators.
The idea, say the researchers, would be to give companies the ability to connect multiple events to help give them a picture of how an attack, particularly one from inside the organization, unfolded over time – and possibly stop one happening in the first place.
"In an idealistic environment any type of malicious activity should be prevented or detected and mitigated but this is almost never the case, especially when the attacker is a trusted authority," the report reads.
"It is the case that many times malicious activity goes undetected for a long period and incidents are not reported in a timely manner."
In one example, researchers said an administrator would respond to an incident by querying the system in SPARQL semantic query language with a set of parameters including things like access logs, device permissions, and surveillance or sensor records. The system will then produce the results with records or a provenance graph showing how the fields intersect.

NSA dev in the clink for 5.5 years after letting Kaspersky, allegedly Russia slurp US exploits
READ MOREThe result would be a clear picture of who was where and what they were doing, both within the network and on the floor of the office itself. The latter, the researchers suggest, is the key to catching insider threats. Even someone with elevated permissions that may never trigger an alarm on the network or servers could get caught on cameras or physical logs.
While the system seems complex, the researchers say that early trials with student volunteer admins showed that the entire system was surprisingly easy to learn. In many cases the volunteers would learn how to perform basic queries on the system and solve the attack scenarios with minimal training.
"All eleven analysts without having any prior experience with the system succeeded to identify the insiders," the researchers said.
"This is mainly based on the intuitive approach the analysts followed to investigate the incidents."
In the end, the researchers believe the framework could be followed by organizations to create systems that would be more flexible than existing security offerings and give a deeper insight into logs and records, allowing admins to catch both isolated incidents and long-running espionage operations. ®