This article is more than 1 year old
Early to embed and early to rise? Western Digital drops veil on SweRVy RISC-V based designs
First look at drive controller core after firm moves to open chip spec
Western Digital today finally flashed the results of its vow to move a billion controller cores to RISC-V designs.
WD said last year it needed an open and extensible CPU architecture for its purpose-built drive controllers and other devices. As we explained then, no one knew for sure what processors WD has used for its disk and SSD controllers, though they was likely Arm-compatible chips – such as Arm9 and Cortex-M3 parts. It is known that the firm uses Intel CPUs with its ActiveScale archive systems and Tegile all-flash and hybrid arrays.
Last year, the disk and solid-state drive manufacturer vowed that RISC-V was its future, and today it announced the SweRV core, a networked cache coherency scheme, and a SweRV instruction set simulator.
The drive-maker's CTO, Martin Fink, said data needs to be closer to compute and general-purpose CPU architectures don't cut it. RISC-V enables open standard interfaces to be used to enable specialty processing, memory-centric designs, unique storage and flexible interconnect applications.
The SweRV core has a two-way superscalar design and is a 32-bit, nine-stage pipeline core, meaning several instructions can be loaded at once and execute simultaneously to save time. It is also an in-order core, whose relative single core performance (a simulated 4.9 CoreMark/Mhz) is expected to exceed that of many out-of-order cores, such as the Arm Cortex A15 (actual 4.72CoreMark/Mhz).
Clock speeds go up to 1.8Ghz and it will be built on a 28mm CMOS process technology.
WD said it hopes open-sourcing the core will drive development of data-centric applications such as Internet of Things (IoT), secure processing, industrial controls and more. We understand WD's ambitions for using RISC-V CPUs go beyond disk and flash drive controllers.
OmniXtend is its open and branded approach to providing cache coherent memory over an Ethernet fabric. Cache coherency ensures that multiple processors, which are sharing cache memory, are in sync.
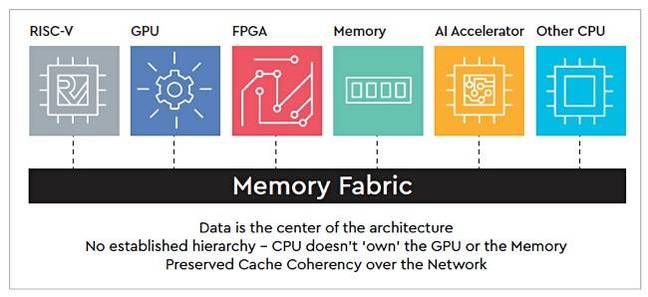
Western Digital's OmniXtend cache coherency graphic
OmniXtend provides open-standard interfaces for access and data sharing across processors, machine learning accelerators, GPUs, FPGAs and other components.
The Register should point out here that disk and SSD controllers have not typically needed a cache coherency scheme and WD's ambitions must lie up the stack at the systems level.
WD said OmniXtend offers potential support of future fabrics that connect compute, storage, memory and I/O components.

WD to move all its stuff to RISC-V processors, build some kind of super data-wrangling stack
READ MOREThat sounds like system composability and WD is already present in the composable systems space with its OpenFlex hardware and software.
To help boost the RISC-V ecosystem and the SweRV design's future, Western Digital is open-sourcing a SweRV Instruction Set Simulator (ISS). It means external events can be modelled – interrupts and bus errors, for example – to ensure a RISC-V core is functioning properly.
+Comment
As WD deploys the vast majority of its cores to disk and flash drive controllers, transferring to RISC-V will be largely invisible to the world outside these embedded systems.
If it develops 64-bit RISC-V technologies and uses these at a systems level, instead of, for example, x86 processors, then RISC-V visibility will become more prominent. Also WD's costs will go down as it will no longer need to buy Intel CPUs or ARM licences for such systems. ®

