This article is more than 1 year old
Fix LibreOffice now to thwart silent macro viruses – and here's how to pwn those who haven't
Remove LibreLogo immediately
Updated See our note below: LibreOffice version 6.2.5, which was supposed to patch the macro security hole, is still vulnerable, and exploit code is now available. Disable LibreLogo immediately if it is present and enabled in your build of LibreOffice. Our amended article follows.
The Document Foundation said on Tuesday that it had recently patched LibreOffice, its open-source office suite, to fix* an issue where documents can be configured to run macros silently on opening.
The code execution vulnerability, reported by Nils Emmerich and assigned CVE-2019-9848, is the result of multiple flaws.
The first is with a feature called LibreLogo which is intended for teaching programming. You type Logo commands into a document and it draws graphics from those instructions with a cursor that looks like a turtle, as a homage to the Logo programming language of yore.
The LibreOffice implementation converts the Logo commands to Python, which is passed to the Python interpreter for execution without much in the way of safety checks. LibreLogo is an optional component, though installed by default.
The second problem is that built-in macros in LibreOffice are fully trusted – including the macro that runs LibreLogo. Even if you set macro security in LibreOffice to "Very high", the LibreLogo macro still runs without prompting. The third, and final, problem is that LibreLogo passes arbitrary Python code in the document to the Python interpreter to execute.
The result is that it is trivial to create a document that includes a malicious Python script in its text, which is executed automatically. We created a document that will pop open the Windows Calculator, as per Emmerich’s example, assigned LibreLogo Run to the Open Document event, and attached it to an email to send to a mark. Microsoft's Outlook helpfully made the document read-only for safety when it was received, but it still obediently ran Calc when the attachment was opened.
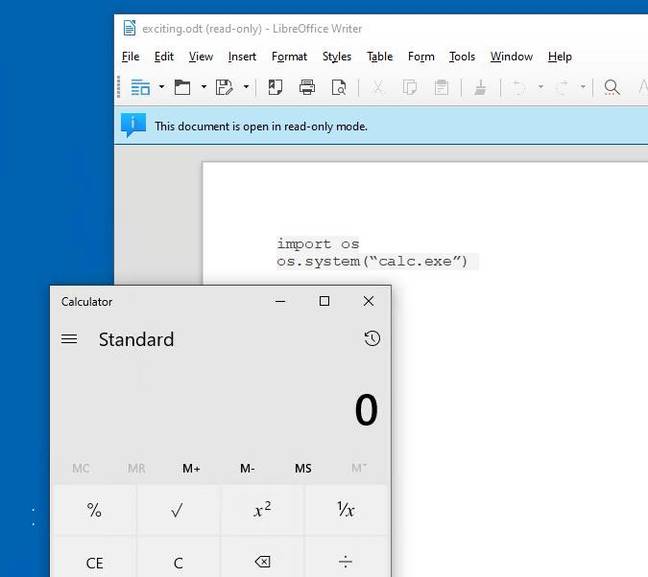
LibreOffice running Calc on Windows 10, without any prompt.
The LibreOffice team tried to fix* the problem by blocking the ability to attach the LibreLogo Run macro to a document event handler. The attempted fix was in version 6.2.5 (released 20 June, 2019).
That said, if you go to the LibreOffice download page version 6.2.5 is recommended only "if you're a technology enthusiast, early adopter or power user". Version 6.1.6 is recommended as it is "tested for longer" and the implication is that it's the pick for more cautious users or businesses. Unfortunately, it is also still vulnerable, as demonstrated in our quick test.
It was Microsoft Word that made macro viruses famous, one of the best known being Melissa in 1999. Much pain ensued, but Microsoft made many efforts to contain the problem, and in Office 2007 introduced the .docm format for Word documents that contain macros, as well as similar formats for other Office applications. There is no such distinction in ODF (Open Document Format) as used by OpenOffice and LibreOffice. Perhaps there should be.
Users of LibreOffice who set it as the default application for .ODT documents should either upgrade to version 6.2.5 or higher, or remove the LibreLogo component from their installation.®
Updated to add at 09:11 UTC on 31 July
*It appears that the supposedly fixed 6.2.5 is still vulnerable – which has been confirmed by us. There are more details over here on Metasploit's GitHub project. An exploit for the security hole has now been added to Metasploit, which is a popular hacking framework.
The proper fix, therefore, on Windows at least, is to go to Control Panel – Programs and Features, hit Change on the LibreOffice entry, and untick the LibreLogo component.
For what it's worth, we cannot find any reference to LibreLogo on our office Debian GNU/Linux systems running LibreOffice 5, though LibreOffice 6.2.4 and 6.2.5 on Debian 9.9 are said to be vulnerable, so the component may or may not be enabled by default everywhere.
To be safe, look for LibreLogo and disable it on sight.

