This article is more than 1 year old
Rethinking VPN: Tailscale startup packages Wireguard with network security
'A whole bunch of tunnels': Mesh networking with per-node permissions and OAuth security
Interview WireGuard, a new VPN protocol with both strong performance and easy setup, has been adopted by startup Tailscale as the basis of a peer-to-peer remote networking system that is both secure and quick to configure.
WireGuard is an open source VPN which achieved its 1.0 release on March 30th, coinciding with the release of Linux 5.6. "Earlier this evening, Linus released [1] Linux 5.6, which contains our first release of WireGuard … for those of you who were scared away prior by the ‘dOnT uSe tHiS k0de!!1!' warnings everywhere, you now have something more stable to work with," said Jason Donenfeld, WireGuard's creator.
According to the white paper, WireGuard "aims to replace both IPsec for most use cases, as well as popular user space and/or TLS-based solutions like OpenVPN, while being more secure, more performant, and easier to use."
The VPN protocol has been well-received (not least by Torvalds) since it lives up to its claims, with both easier setup and better performance than alternatives.
WireGuard is by design small (just 4,000 lines of code) and dedicated to a single purpose: connecting a client to a server over a VPN. This leaves plenty of scope to build complete VPN solutions around it, or to integrate into existing ones, which is exactly what has been happening. NordVPN, for example, offers NordLynx built on WireGuard, but with double NAT (Network Address Translation) to protect privacy. Concerning WireGuard, NordVPN told us that "Its simplicity, ease of implementation and management are likely to significantly surpass OpenVPN, and WireGuard's encryption speed blows the IPsec group protocols out of the water."
The new protocol is also an opportunity for startups, one being Tailscale, formed in March 2019 six months after its co-founder and CEO Avery Pennarun left Google, where he was a senior engineer working on Google Fiber.
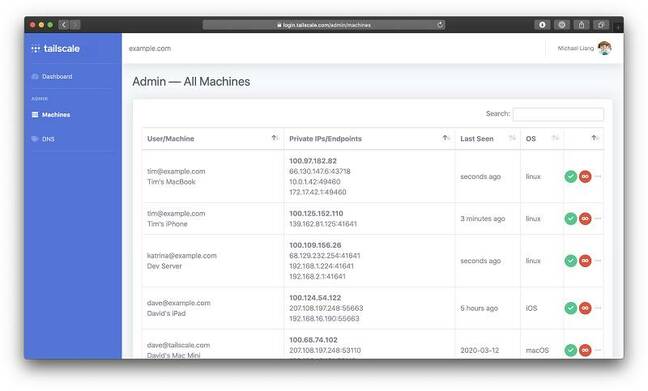
Tailscale's product includes several pieces. First, it's based on peer-to-peer VPNs rather than piping all VPN traffic through a single concentrator. WireGuard security uses public keys. One endpoint can connect to another if it knows the public key and the UDP endpoint (IP address and port) to connect to. Tailscale maintains a database of endpoints on its server, so that when client A needs to talk to client B, it fetches the endpoint details and then makes a direct connection. Tailscale calls this a mesh network.
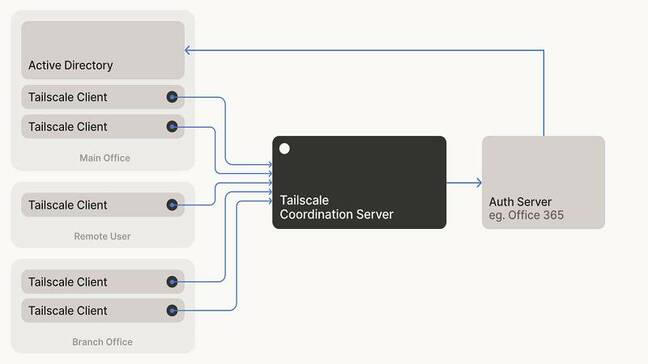
Tailscale clients retrieve connection information from a server, but no other data passes through the server
Second, Tailscale authentication is always outsourced to an OAuth2, OpenID Connect or SAML provider, such as an Azure AD or Google G Suite login. Third, NAT traversal is built in so that you can connect without opening firewall ports. If UDP is blocked completely, it can use HTTPS streams.
Finally, there's a per-node permission system, so you can specify to which IP addresses and ports a user is allowed to connect.
Vulture has a go
We gave Tailscale a quick spin, admittedly with only two Windows PCs. One was on Azure, the other behind two firewalls. Login to Tailscale redirects to your chosen provider, in our case Azure AD (you can also use any Google account).
That done, it was a matter of installing the client on the two PCs, logging in, and noting the IP numbers assigned by Tailscale to them.
Then we were able to open a remote desktop connection from one to the other; everything worked as promised with no further configuration. By default there is no DNS and no routing - in other words, PC A can ping PC B, but not other machines on the remote network unless they also have Tailscale installed, and you need to know the IP numbers.
You can fix this by setting up DNS and routing yourself, though note that if you route all the traffic for a network through one server, you are not benefiting from the Tailscale mesh. There is an explanation of the system here.
Pennarun spoke to The Reg, beginning with an explanation of the company name. He says that Google's massively scalable infrastructure adds complexity, and that "teams that I had seen while I was at Google were forced to use this sort of overkill infrastructure, even for their small problems. The joke is that 'tail' scale is the opposite of Google scale."
According to Pennarun, the company was initially more interested in network security than VPNs. An early customer, a bank, wanted to secure a old but critical Windows application, and rather than updating it to use two-factor authentication, he proposed: "Why not move the server into its own little network, so that people can only access that network after they've done two-factor authentication? That was the origin of building this tool. It wasn't intended as a remote access VPN, it was intended as a local access VPN. We did base it on WireGuard because WireGuard was an efficient data plane for their system. It turned out that the core thing we build, this multi-point VPN, was applicable to all sorts of other problems."
Most of the trouble of setting up IPsec is just getting IPsec to work at all. WireGuard eliminates all that complexity. It's just five settings, and now you've got a tunnel. That gives us a building block to construct a whole bunch of tunnels...
WireGuard, he says, "eliminates a whole bunch of things that can go wrong when you're building a VPN. Most of the trouble of setting up IPsec is just getting IPsec to work at all. WireGuard eliminates all that complexity. It's just five settings, and now you've got a tunnel. That gives us a building block to construct a whole bunch of tunnels."
The security aspect then is equally as important as the networking. The idea is to get away from the problem that "as soon as someone gets through your firewall, it's a free-for-all. The modern solution to this is zero trust networking, traditionally done at the application layer, with zero trust for the network itself."
With Tailscale though, "you can only connect to the nodes that you should have access to. You put a Tailscale engine on every single server you want to secure, then Tailscale/WireGuard encrypts the traffic all the way to the node itself, decrypts it locally. So you don't have this problem of ever going over the physical wire unencrypted. It's a lot like the zero trust network, but it has the advantage of being at the IP layer, instead of at the HTTP layer. That means it will work with any application," he says.
"Something simple like Microsoft Access or Windows file sharing now has the security in the core layer instead of on top."
How are the permissions configured? "We have a web dashboard but it's in its early stages. It's basically an editor for a JSON file, a list of groups of users who can access groups of machines and port numbers."
It should be noted that this kind of setup, with Tailscale used even on internal networks, is not required, nor even is the mesh networking. "If you've already got a VPN between all your data centres, the easiest way to use Tailscale is to just put one subnet router into a data centre. Now your users who are remote can connect to that one subnet router. It's very much like a straightforward point-to-point VPN. But it's no worse than you had before."
Since all the big VPN providers seem to be adopting WireGuard, at least as an option, why use Tailscale? "Wireguard is a data plane," says Pennarun. "It does the same job as an IPsec tunnel or various other tunnels. But what they don't do is the two-way NAT traversal that we do. My laptop and my phone can be in different locations between different firewalls and can talk to each other directly. The other part is that key exchange ties into your existing identity system."
Tailscale is a small company and the usual cautions apply. "We're about 10 people," Pennarun tells us, as well as being "a fully remote company. All three founders are in a different city."
The usual cautions apply; but as it turns out, the current crisis, with huge numbers of newly remote workers, has increased demand for VPN solutions, and highlighted some issues with existing ones. "There are a lot of people running into physical limits of their VPN hardware. IPsec is a very CPU intensive protocol," he says. "We have a lot of people kicking the tyres right now. But nobody's deployed it to 10,000 people yet." ®