This article is more than 1 year old
If you want to hijack widely used JavaScript packages, try phishing for devs through these DMARC-shaped holes in key Node.js domains
npmjs.com, nodejs.org open to spoofing, we're warned
Two significant domains for the Node.js community, npmjs.com and nodejs.org, lack DMARC email security policies, an oversight that could allow a miscreant to send easily spoofed emails to the community.
The Register was alerted to the issue by a developer using the pseudonym niftylettuce who expressed concern that forged emails of this sort could facilitate phishing attacks aimed at hijacking user accounts to gain control of widely used npm packages.
Many domains have not implemented DMARC, leaving open the possibility of domain spoofing in email messages. But the potential consequences of a successful phishing attack against an npm package author are particularly worrisome because mass malware distribution via the hijacked account might then be possible.
In recent years, there have been several noteworthy attacks on developer accounts.
"This would be the simplest attack I've ever seen and require basically zero effort," niftylettuce said, noting that it would be trivial to scrape GitHub and npm for user account email addresses in order to spam them with phishing messages that appear to come from one of those two websites.
Is DMARC dead to them?
Domain-based Message Authentication Reporting and Conformance (DMARC) allows domain owners to specify how to handle unauthorized use of their domain name for email. DMARC records are text strings published as part of the domain's DNS record that declare an email policy when SPF and/or DKIM checks – two email authentication schemes – have been evaluated.
DMARC policy declarations – key/value pairs within the full string – can be p=none, p=quarantine, and p=reject. Without a DMARC setting, there's the potential for abuse.
A complete DMARC entry looks something like this:
v=DMARC1; p=reject; rua=mailto:mailauth-reports@example.com
Attacks of this sort may rely on a forged From: address or may rely on a lookalike domain, such as npmjs.io.
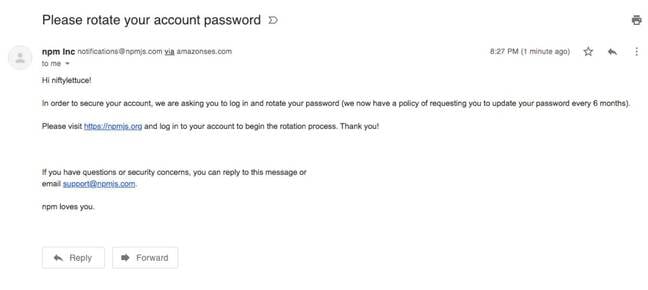
To demonstrate how easy it would be to launch a phishing attack targeting Node.js developers, niftylettuce sent himself a spoofed npmjs.com email via Amazon SES (which npmjs.com uses without a DKIM signature), which you can see below and which could lead marks to a faked password reset page to harvest credentials:
"This could land in every npm user's inbox (because DMARC isn't implemented), and presumably a large percentage would fall for the phishing attack," niftylettuce explained in an email. "It's super easy to clone npm's website, as their website's historical source code is open source on GitHub."
With a developer's npm credentials in hand, packages maintained by the developer could easily be subverted through the addition of malicious code. "If this breach happened, the entire npm database would need a password reset and will be locked out," niftylettuce wrote.
The Register asked Microsoft's GitHub, which acquired npm in March, whether it sees this as a serious security issue. We were told that GitHub is looking into implementing DMARC but is going slowly to ensure that configuration changes don't have unintended consequences like hindering email deliverability. ®