This article is more than 1 year old
Hyper-V bug that could crash 'big portions of Azure cloud infrastructure': Code published
Now patched: 'A function that can be called with attacker-controlled data (which it shouldn't) and dereference twice a pointer (boom)'
Security researchers have posted proof of concept code that exploits a recently patched vulnerability in Microsoft's Hyper-V hypervisor. The bug enables code in the guest to crash the host, and in some circumstances compromise the host's security.
A fundamental principle of virtualization is that the virtual machine guests are isolated from the host server and from one another. Vulnerabilities that breach this barrier are particularly serious for hosting companies, since they raise the possibility of one customer seeing data that belongs to another, or criminal intrusions into the hosting company's infrastructure.
This issue, CVE-2021-28476, was patched by Microsoft on May 11.
You little BSOD
Microsoft said it "allows a guest VM to force the Hyper-V host's kernel to read from an arbitrary, potentially invalid address. The contents of the address read would not be returned to the guest VM."
It continued: "In most circumstances, this would result in a denial of service of the Hyper-V host (bugcheck) due to reading an unmapped address. It is possible to read from a memory mapped device register corresponding to a hardware device attached to the Hyper-V host which may trigger additional, hardware device specific side effects that could compromise the Hyper-V host's security."
A bugcheck, also known as a blue screen of death, crashes the host. This meant that anyone with a VM on Azure would have been able to crash one of Microsoft's servers, though normally that is the limit of the damage. In theory this could escalate to remote code execution on the server, but this is unlikely since it relies on knowledge of the address of a memory-mapped device. The vulnerability is nevertheless critical.
Security researcher Axel Souchet, who maintains a blog called Diary of a reverse-engineer, has now posted proof of concept code which enables anyone to blue-screen an unpatched Hyper-V host via code running in the guest.
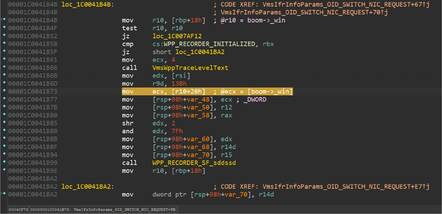
"The bug itself happens in VmsIfrInfoParams_OID_SWITCH_NIC_REQUEST which is a function that can be called with attacker-controlled data (which it shouldn't) and dereference twice a pointer (boom->_win below) that a malicious guest virtual machine can provide," said Souchet.
4 stories
- Microsoft emits more fixes for Exchange Server plus patches for remote-code exec holes in HTTP stack, Visual Studio
- Penguin takeover: We tried running some GUI Linux apps on Windows the official way – and nothing exploded
- What's in Fedora 34? GNOME 40, accelerated Wayland, PipeWire Audio, improved Flatpak support, and more
- The first rule of ERP? Don't talk about ERP: App-maker IFS reckons market has moved on
Users cannot just remote desktop into a Windows VM and run some code: the posted exploit requires Ubuntu Focal and a kernel rebuild.
Discovery
The issue was discovered by researchers Leo Adrien and Daniel Fenandez at Blue Frost Security, Peleg Hadar of SafeBreach Labs, and Ophir Harpaz at Gardicore Labs. Hadar and Harpaz are presenting a session at the forthcoming Blackhat USA conference about how the bug was discovered using fuzzing tools specially adapted for Hyper-V. The presenters said they promise "a live demo of exploiting this vulnerability, which until only a few weeks ago could take down big portions of Azure cloud infrastructure."
While Microsoft will presumably have been quick to patch Azure, the same may not be true of other Hyper-V installations. Hosting companies are the most vulnerable since any customer may run up a virtual machine, though most hosting providers run Linux-based hypervisors. Enterprise installations accessed only by trusted employees are less at risk, though it still is a critical vulnerability and should be patched as soon as possible if it has not already been done.®