This article is more than 1 year old
Mysterious Gelsemium APT was behind February compromise of NoxPlayer, says ESET
Malicious crew targets ME and Asia but also tries evading Chinese AV suites
ESET has published details of an advanced persistent threat (APT) crew that appears to have deployed recent supply chain attack methods against targets including "electronics manufacturers," although it didn't specify which.
“Victims of its campaigns are located in East Asia as well as the Middle East and include governments, religious organizations, electronics manufacturers and universities,” said ESET in a research report published today that names the APT crew as Gelsemium.
Those target countries include China, Japan, Mongolia, Taiwan, North and South Korea, and various Middle Eastern countries according to a map drawn up by ESET. The miscreants’ malware, however, has previously included bypasses intended to evade Chinese-made antivirus suites.
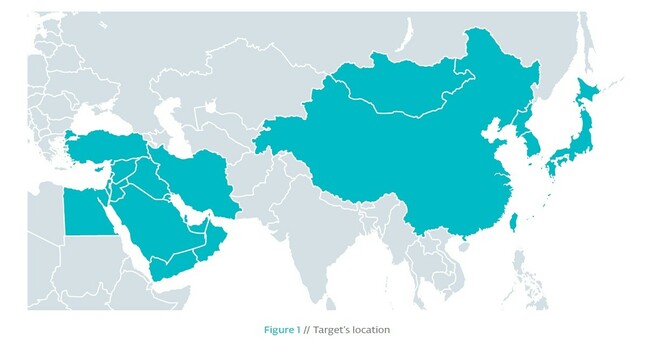
ESET illustration showing Gelsemium's known targets
Gelsemium is said to have been behind a supply chain attack targeted at a freeware Android emulator called NoxPlayer, made by BigNox, which boasts of having about 150 million users in total worldwide.
In an incident highlighted by ESET in February before attribution to the APT, BigNox’s update API mechanism may have been compromised to deliver malware to selected users under the guise of a legitimate new version.
First seen in the mid-2010s, Gelsemium has used delivery vectors ranging from plain old spear-phishing at its outset to abuse of the Microsoft Exchange vulnerability seen in Q1 of this year.
Discovery of new APTs is not unusual but still adds to the wider body of infosec knowledge and it certainly makes a change from endless analysis of ransomware gangs’ activities; a valuable lesson that not every threat facing internet-connected organisations today is the one making mainstream telly news headlines.
“During our investigation we found victims where Mimikatz was dropped on machines. The operator uses a Powershell version of the tool, downloaded from a remote server,” added ESET.
The antivirus company, which is based in Slovakia, gave a grateful nod to other infosec research firms in its whitepaper, citing work from companies based as far afield as China itself. Back in 2018 Chinese infosec firm Venustech published (PDF, in Chinese) a paper about what ESET now calls Gelsemium, with one concluding sentence in particular sticking out: “The malware delivered from this organization contains a large number of detection and circumvention methods for Chinese anti-virus software.”
ESET itself highlighted in its own analysis that Gelsemium’s malware payload included checks for, among other common consumer endpoint antivirus suites, Qihoo360 and Kaspersky.
The firm's Thomas Dupuy told The Register: “This antivirus detection is a bit complex, it is used to tweak the behavior of the malware. For example, stopping the execution of certain processes or mechanisms used to drop the next stage and sometimes terminate the execution of the malware. On top of that, standard user or administrator and Windows version add more versatility. For example, if 360 AV is installed and the Windows version is before Windows Vista it terminates the execution.”
More information is available on ESET’s blog. ®
