This article is more than 1 year old
Iranian state-backed hackers posed as flirty Scouser called Marcy to target workers in defence and aerospace
Recognise this one? Oh dear...
Iranian state-backed hackers posed as a flirty Liverpudlian aerobics instructor in order to trick defence and aerospace workers into revealing secrets, according to a newly-published study.
Researchers from Proofpoint said this morning they had uncovered a fake social media account being operated by state-backed Iranians, tracked internally by the enterprise security firm as TA456.
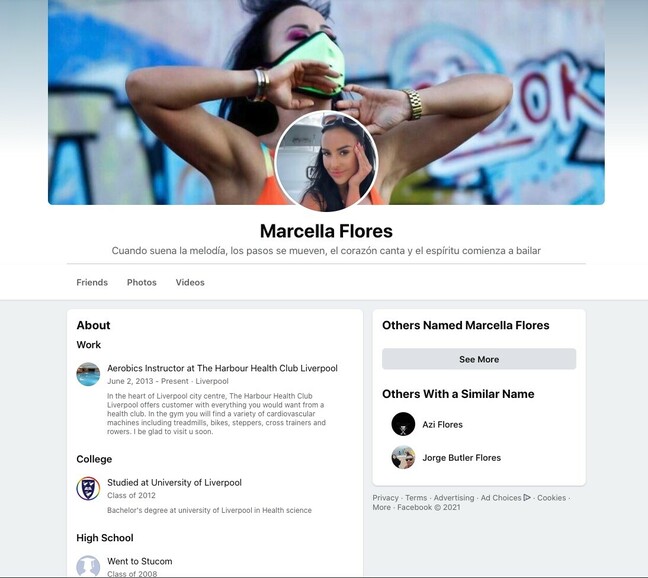
Using the alias Marcella Flores, the Iranians patiently built up a relationship with their targets "over years" to convince them to open malware-laden emails on useful devices – even sending a video of "herself" to sucker in her unwitting targets.
"Once the malware, which is an updated version of Liderc that Proofpoint has dubbed LEMPO, establishes persistence, it can perform reconnaissance on the infected machine, save the reconnaissance details to the host, exfiltrate sensitive information to an actor-controlled email account via SMTPS, and then cover its tracks by deleting that day's host artifacts," said the infosec outfit in a blog post published today.
Variously known as Imperial Kitten and Tortoiseshell, the Iranian crew tracked by Proofpoint apparently has a taste for using western female aliases. In the case of Marcella "Marcy" Flores, they went a little deeper than has previously been seen in public.
A screenshot of "her" now-deleted Facebook page showed an unremarkable profile that wouldn't have raised questions in a non-friend's mind – exactly as it was intended to be.
"The 'Marcella' profile appeared to be friends with multiple individuals who publicly identify as defense contractor employees and who are geographically dispersed from 'Marcella's' alleged location in Liverpool, UK," said Proofpoint.
- America world's sole cyber superpower, ten years ahead of China, says Brit think tank
- Dozens of Iranian media websites devoured by the Great Satan, apparently
- Iran bans cryptocurrency mining for four months as the weather – and election campaigns – start to heat up
- SAP to pay $8m in non-prosecution agreement with US authorities over Iran sanction violations
South of Liverpool is the Airbus wing factory at Hawarden, just inside the Welsh border. A couple more miles brings you to another Airbus factory at Broughton, which among other things carries out final assembly of Eurofighter Typhoon jets for European air forces. It takes little to imagine engineers at either location potentially chatting to what they believed to be a local girl – though Proofpoint did not name the contractors involved.
The takedown of "Marcy" came when Facebook summarily deleted a bunch of Iran-related mischief from its website earlier this month, highlighting fake accounts "designed to attract particular targets within the aerospace and defense industries" and deceive the victims into visiting credential-harvesting sites.
Symantec previously published detailed research into Tortoiseshell, setting out its targeting of IT companies in supply chain attacks. Cisco Talos has also found it targeting US military leavers hunting for jobs.
While there appears to be significant overlap between Tortoiseshell, Imperial Kitten, and APT35, there is no consensus on whether the APT is one and the same as the featured hacking crew above. ®