This article is more than 1 year old
Google's VirusTotal reports that 95% of ransomware spotted targets Windows
Criminals follow the money, code flaws
Google's VirusTotal service showing that 95 per cent of ransomware malware identified by its systems targets Windows.
VirusTotal, acquired by Google in 2012, operates a malware scanning service that can be used manually or via an API, to analyze suspicious files. The team collected data between January 2020 and August this year to investigate how ransomware is evolving. VirusTotal receives over two million suspicious files per day from 232 countries, it said, placing it in a strong position to analyse the problem.
Over the period there are at least 130 different ransomware families, the report said, and change is constant. "It seems that in most cases attackers prepare fresh new samples for their campaigns," the report states.
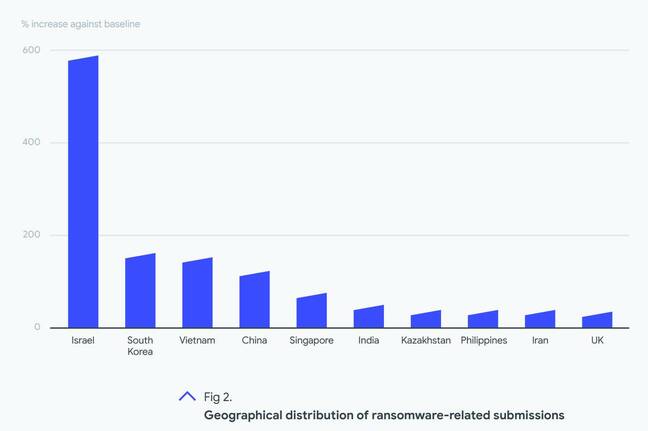
There were notable geographic distinctions, with Israel submitting by far the most ransomware samples, follows by South Korea, Vietnam and China. The UK is 10th. This does not necessarily mean that these territories were the most attacked though. VirusTotal security engineer Vicente Diaz, in a video presentation, said that the high figures for Israel "could be related to many companies [there] automating their submission."
In other words, territories which are more diligent in submitting samples will show more positives, so a high figure may indicate better defences rather than more attacks, or perhaps both.
Getting their claws in
The top family of ransomware was one dubbed Grandcrab, accounting for 78.5 per cent of positive samples, largely thanks to a spike in activity between January and July 2020. In July 2021 there was another spike, this time for Babuk.
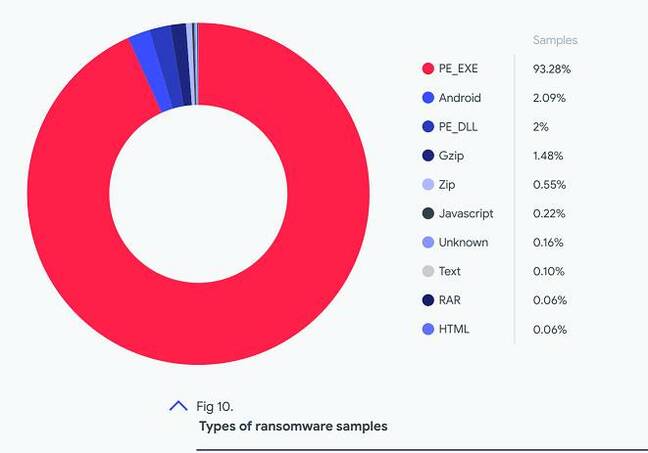
What systems are most attacked? 93.28 per cent of ransomware detected were Windows executables, and 2 per cent Windows DLLs, the report said. "This is not a surprise … most of this malware is meant for Windows Systems," said Diaz. Android accounts for just over 2 per cent of the files, and around mid-2020 a number of positive samples, called EvilQuest, were identified, targeting the Mac.
In the presentation, Diaz also addressed the key question of building an effective anti-ransom strategy. Detect the well-known malware, he said, and ensure a patching strategy that prioritised privilege escalation issues such as SMB (Server Message Block, the Windows network file sharing protocol) vulnerabilities.
- When criminals go corporate: Ransomware-as-a-service, bulk discounts and more
- Ransomware crim: Yeah, what I do is bad. No, I don't care. Yes, infosec bods are all mouth and no trousers
- US invites friends to multilateral cybersecurity meetings – Russia and China strangely absent
- Never mind Russia: Turkey and Vietnam are Microsoft's new state-backed hacker threats du jour
Scripting languages, he said "are very easy droppers that the attackers can use," and increasingly taken advantage of, so he suggests hardening and restricting them where possible. Monitor new waves of ransomware, he said. Finally, and possibly most important, he advised implementing cyber resilience strategies, meaning we surmise well-protected backups and tested recovery strategies.
While this is sound advice its implementation can be challenging. The Windows printing system has proven to be an escalation of privilege vulnerability, for example, and although it can be mitigated Microsoft has not fixed it completely and some administrators have struggled to follow best practice without breaking functionality.
It's where the money is
Why is Windows so prominent? There are several factors, including massive market share and ubiquity, the value of the targets, and the fact that legacy code in Microsoft's operating system is hard to secure.
"Our Chrome OS cloud-first platform has had no reported ransomware attacks … on any business, education or consumer Chrome OS device," brags Google.
When Microsoft has tried to establish more locked-down editions of Windows though, such as Windows RT and Windows S, it has met resistance from users unable to run the software they need. Google with Chrome OS, and Apple with iOS, designed new operating systems with security in mind.
VirusTotal's report measures the malware it has detected, and not successful attacks. In general, malware submitted to VirusTotal has probably been unsuccessful, since it has been detected.
There are also other vectors of attack, such as phishing, or exploiting bugs and vulnerabilities in network appliances, the majority of which run Linux. The overall picture may not be quite as Windows-dominated as it first appears. That said, security Microsoft's operating system looks set to remain a key challenge for the industry. ®