This article is more than 1 year old
The inside story of ransomware repeatedly masquerading as a popular JS library for Roblox gamers
Ongoing typosquatting attacks target kids as Discord drags its feet
Since early September, Josh Muir and five other maintainers of the noblox.js package, have been trying to prevent cybercriminals from distributing ransomware through similarly named code libraries.
Noblox.js is a wrapper for the Roblox API, which many gamers use to automate interactions with the hugely popular Roblox game platform. And for the past few months the software has been targeted by "a user who is hell-bent on attacking our user-base with malware, and continues to make packages to this end," explained Muir in an email to The Register.
This miscreant, with the assistance of at least one other, has been "typosquatting" the noblox.js package by uploading similarly named packages that deliver ransomware to NPM, a registry for open source JavaScript libraries, and then promoting the malware-laden files via Discord, a messaging and chat service.
Last month, security firm Sontatype published a blog post about the poisoned noblox.js lookalikes, but dismissed this particular software supply chain compromise as a likely prank.
Muir begs to differ. "I believe Sonatype described this attack as a potential 'prank' – I assure you it is not, but more a persistent and continuous attack on our library and its users," he said.
No prank, someone's stalking kids
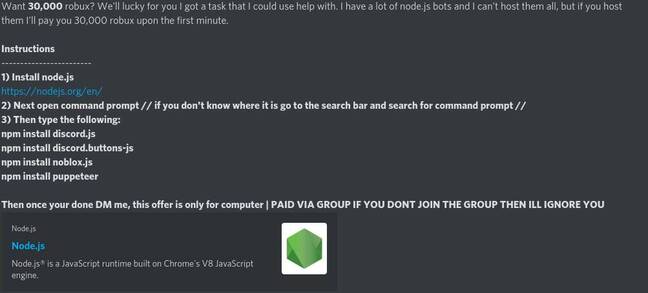
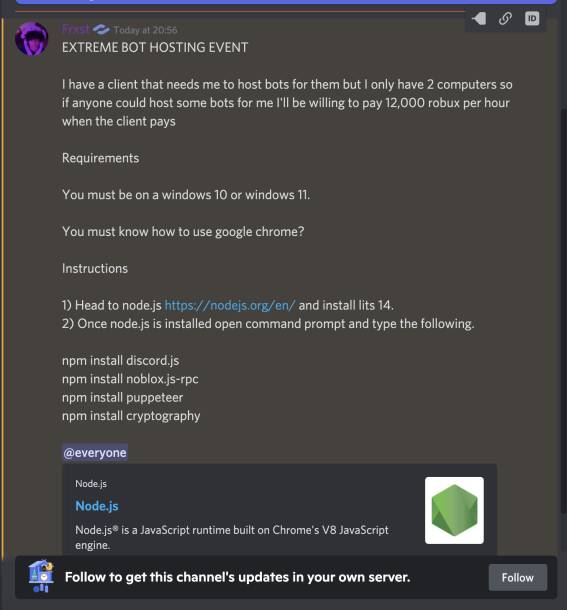
Muir said he's aware of at least six libraries created with confusingly similar names, to dupe the unwitting unto downloading the compromised code rather than the legitimate noblox.js library.
noblox.js-rpcnoblox.js-proxynoblox.js-betanoblox.js-promisenoblox.js-promisesdiscord.buttons-js
"We have reported all of these, and noblox.js-rpc is the only one currently online," said Muir in a message on Sunday. "The first of these attacks, discord.buttons-js, was created as long ago as the 7th September, and was the first. Despite its title relating to Discord, it had the noblox.js Readme file."
Since then, noblox.js-rpc has been flagged and removed.
@malwrhunterteam malicious npm package: noblox.js-rpc
— Gladiator (@Lonegladiator_) November 14, 2021
Seems to behave like ransom, except without the locking of files, only the overwriting of MBR pic.twitter.com/JyPKVQU0QM
In an email to The Register, Ax Sharma, a senior security researcher at Sonatype, confirmed that the company is seeing more and more malicious NPM packages, including another noblox.js typosquat called noblox.js-rpc that the security firm reported to NPM.
"The package is by the same threat actor who had previously published fake Noblox packages delivering ransomware," said Sharma. "The threat actor also maintains a Discord server to share information on the infected repositories, and solicit ransom amounts from impacted victims."
Discord not exactly on form
Sharma said this isn't the first time Discord has been used by threat actors to collaborate on and host malicious payloads. He pointed to the CursedGrabber NPM malware that Sonatype spotted a year ago. It used Discord attachments to serve malware and webhooks to exfiltrate data.
"Because some of these typosquats are cleverly named, differing just by a character from the name of the legitimate package, it is plausible some developers were infected by these packages, although the full scope of the impact remains unknown and yet to be assessed," said Sharma. "We are not aware of any Sonatype customers being impacted by these malicious packages thus far."
Indeed, the target audience appears to be kids. Minors represent the majority of those using noblox.js.
Muir said those responsible are spreading malware by joining Discord servers with young users – according to Roblox, "[T]he majority of our users are under the age of 13" – to gain a position of trust and convince them to download a compromised library.
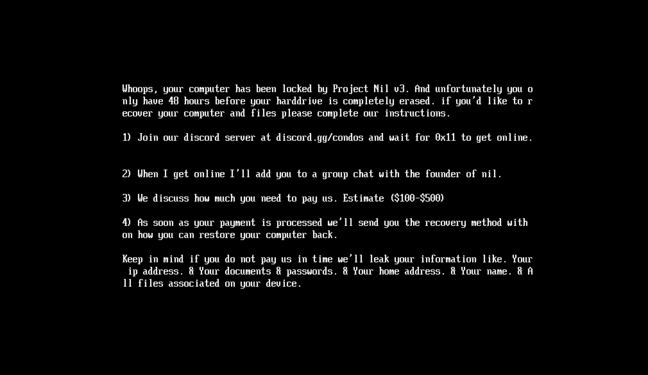
Messages like this, Muir said, are frequently shared through a Discord-hosted "Condos" server – a reference to a Roblox game called "The Condo" that depicted sexually explicit game characters and was shut down by the company, though the term lives on as a pointer to explicit material.
"Looking purely at the number of installs for these packages, we estimate somewhere around 200 users have installed the malware," said Muir. "It is difficult to determine an exact total, as several of the packages have artificially inflated install counts – we presume to make them appear more legitimate."
Muir said among those who appear to have been victimized, he or his fellow maintainers have been in touch with four of them. He provided a screenshot of the "Condos" server that's used as a callback point for victims to arrange payment to have their ransomed files released. (There are many "Condos" servers.)
One of his fellow maintainers, he said, had loaded up the ransomware in a virtual machine and noted that it references the discord.gg/condos server.
Muir said he has reason to believe at least one minor was blackmailed with stolen files and that this has been reported to Discord.
- NPM packages disguised as Roblox API code caught carrying ransomware
- GitHub fixes authorisation vulnerability in the NPM JavaScript package registry
- Never mind the trolls, Discord hosts 'significant volumes of malware' in its CDN
- About half of Python libraries in PyPI may have security issues, boffins say
While GitHub's NPM has been reasonably responsive to takedown requests, Muir said, Discord hasn't been nearly as attentive.
"Discord generally doesn't deal with these issues if the original messages are deleted, and the user in question frequently deletes his messages or uses alternate accounts to avoid action," explained Muir. "This is even the case if we report the messages and then they are deleted – which means in the majority of cases, offenders are not caught."
Discord, according to security firm Sophos, has become a popular malware distribution channel and is commonly used for malware command-and-control messaging.
Odd timing
Reports submitted to Discord's Trust & Safety team, Muir said, have been delayed or ignored. He said he submitted a ticket on November 1st and heard back on November 3 asking him to provide an urgency level so Discord could triage his request. He said he marked it as urgent and two weeks on there's been no action taken.
"That being said, Discord's lack of action is somewhat shocking given the Discord server in question has the invite discord.gg/condos, and is primarily dedicated to the creation of depraved Roblox condos, which are sex games aimed at minors," said Muir. "This server has 50,000 members, so it is by no means a small server."
He speculates that some of these are fake bot accounts, but said there were 12,000 online at the time he wrote The Register, which suggests at least some of those accounts are real.
On Monday, about an hour after The Register asked Discord for comment, Muir received a note from Discord's Trust & Safety Team stating that they've opened an investigation.
"Platform security is a priority for us. Discord relies on a mix of proactive scanning – such as antivirus scanning – and reactive reports to detect malware and viruses on our service before they reach users," a Discord spokesperson told The Register.
"We also work proactively to locate and remove communities or individuals misusing Discord for this purpose. Once we become aware of these cases or bad actors, we remove the content and take appropriate action on any participants." ®