This article is more than 1 year old
Not only MSPs: All cloudy firms are in line for UK security law crackdown
Now's a good time to read up on Cyber Essentials Plus
A government crackdown on British MSPs' security practices is drawing ever closer after the Department for Digital, Culture, Media and Sport (DCMS) floated plans to make Cyber Assessment Framework compliance mandatory.
Digital Minister Julia Lopez said in a canned statement: "We are taking the next steps in our mission to help firms strengthen their cyber security and encouraging firms across the UK to follow the advice and guidance from the National Cyber Security Centre to secure their businesses' digital footprint and protect their sensitive data."
Some form of NCSC-accredited certification for managed service providers (MSPs) and cloud firms seems likely to become mandatory in the medium term. They follow on from a government consultation run over summer asking for views about regulating MSPs alone.
In a sign that the regulatory sands are shifting, however, the government said in a public response this week that "any future policy should consider this broader range of digital technology providers, moving away from an exclusive focus on managed services."
Better security in UK.gov's eyes appears to mean MSPs and other cloud service providers will have to comply with the NCSC-backed Cyber Assessment Framework (CAF) "or a framework based on it," industry feedback to the government-sponsored survey said.
- The UK loves cybersecurity so much, it's going to regulate managed service providers' infosec practices in law
- Russia-based criminals are still the UK's number 1 cyber-foe, NSO Group's wares a 'red flag' says NCSC chief
- Sysadmins: Why not simply verify there's no backdoor in every program you install, and thus avoid any cyber-drama?
- UK umbrella payroll firm Giant Pay confirms it was hit by 'sophisticated' cyber-attack
That feedback continued: "Many submissions voiced concerns regarding the government's intention to place additional requirements on an entire UK digital sector. Developing definitions and establishing clear boundaries between various providers of digital technology solutions, including cloud and managed services, remains a challenging task for this government."
Industry is said to have told DCMS it wants more "prescriptive requirements" than the CAF provides for, however, including "formal certification with auditing" and an "obligation to report incidents".
If these are accurate reflections of what DCMS was told, it points the way towards Cyber Essentials Plus potentially becoming the baseline MSP/cloud security standard for British businesses – if DCMS adopts these calls for compliance monitoring of whatever security framework it picks.
Cyber Essentials (without the plus) is already the baseline security standard for government suppliers, though in essence it's a self-assessment checklist.
Meanwhile, existing UK security questionnaire advice isn't really being used:
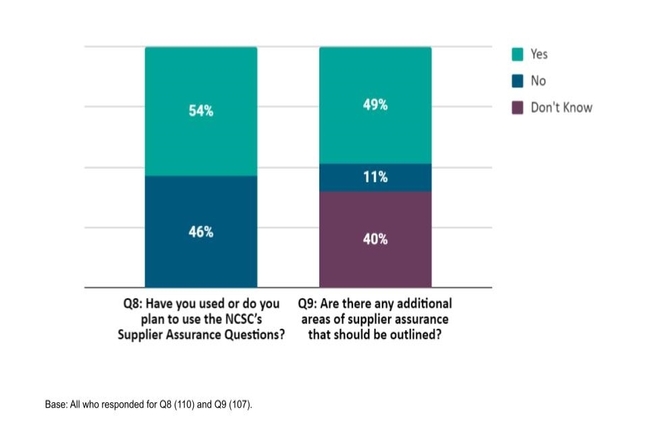
Graph showing half of UK cloud service buyers aren't using supplier security questionnaire
As for buyers of MSP services, they were all in favour of more regulation (or so the would-be regulators at DCMS said) with an interesting caveat about Big Tech:
Many respondents argued, for example, that they cannot make fully informed procurement decisions because it is increasingly difficult to obtain the necessary cyber security assurance from providers who are reluctant to provide information on their cyber security measures or standards they adhere to. This poses a number of business and operational challenges for customers who ultimately bear the risk of cyber security incidents.
Government focus on supply chain security was galvanised by high-profile MSP attacks such as Kaseya in the US. The MSP was compromised by attackers targeting its VSA endpoint and network management tool, giving instant visibility into most of its customers. Similar recent attacks saw firms such as US network management outfit SolarWinds targeted by a Russian espionage agency, among large numbers of smaller attacks.
Not all UK MSPs are as dedicated to good security practices as one might hope, however, as a lighter (but cautionary) ransomware recovery tale from 2019 showed. ®
