This article is more than 1 year old
Microsoft's Secure Boot fix sends some PCs into BitLocker Recovery
Have your BitLocker key handy when updating, but maybe not on a Post-it stuck to the screen, OK?
Windows users are reporting BitLocker problems after installing last week's security update for Secure Boot.
The issues are related to KB5012170, which is designed to plug some Secure Boot holes. It's important for users running kit with Unified Extensible Firmware Interface (UEFI) firmware. "A security feature bypass vulnerability exists in secure boot," wrote Microsoft. "An attacker who successfully exploited the vulnerability might bypass secure boot and load untrusted software."
The patch adds the signatures of the known vulnerable UEFI modules to the Secure Boot Forbidden Signature Database (DBX).
Alas, it appears to do a bit more than that. Lurking in the known issues are warnings that some OEM firmware won't allow the update to be installed. The update might also fail to install with certain BitLocker Group Policy configurations or an 0x800f0922 might be thrown up.
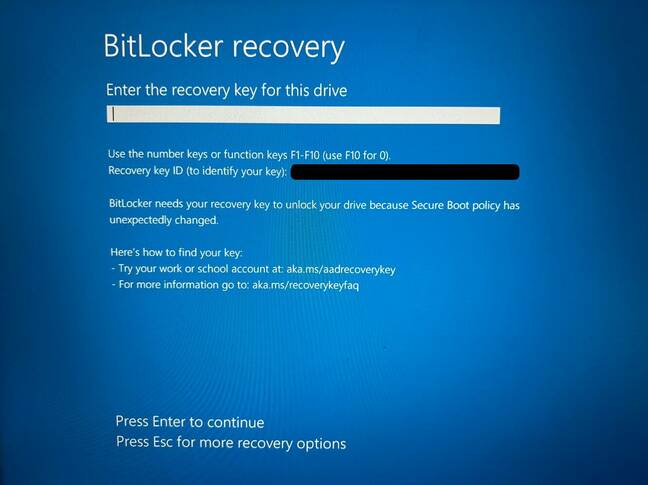
Then there is the tripping of BitLocker recovery, which is not currently listed as a known issue.
The problem occurs on boot, and bring up the BitLocker Recovery screen into which a user is supposed to enter a key.
The depressingly familiar groundswell of grumbling has got under way as a few users have found themselves with unbootable computers unless they can provide the magic key.
Register reader Anthony got in touch to tell us that out of the 400 PCs his company managed, 2 percent (all Windows 11) booted to a BitLocker recovery screen after the update.
- Microsoft's fix for 'data damage' risk hits PC performance
- AMD confirms Ryzen chips' stuttering performance on Windows 10, 11
- User locked out of Microsoft account by MFA bug, complains of customer-hostile support
- Azure flings out free virtual trusted platform module for cloudy VMs
"There is seemingly no way around it if the user doesn't have the key, which is the case most of the time!"
BitLocker is a drive encryption feature aimed at keeping data secure. The recovery process restores access to data and requires the user to supply a lengthy password (or a domain administrator can get the password via Active Directory Domain Services). Anthony told us he was able to log into Azure and retrieve the recovery keys.
"This is the sort of thing the average user would certainly not be able to do," he said. "For some of them it was easy, for others it was a detective game to find out which licence was assigned to which computer."
As for what the patch did to cause the problem, there are a variety of candidates (if one discounts attack attempts). One potential cause listed by Microsoft in its BitLocker documentation is "upgrading critical early startup components, such as a BIOS or UEFI firmware upgrade, causing the related boot measurements to change."
The Register asked Microsoft for an explanation and will update should the company respond.
In the meantime, it would probably be worth at least knowing how to get hold of your recovery key before hitting the update button. Just in case. ®