Robot can rip the data out of RAM chips with chilling technology
'The more important a thing is for the world, the less security it has' says inventor
Cold boot attacks, in which memory chips can be chilled and data including encryption keys plundered, were demonstrated way back in 2008 – but they just got automated.
That original type of attack has been improved and automated in the form of a memory-pilfering machine that can be yours for around $2,000, with a bit of self-guided electrical fiddling.
On Friday, at the REcon reverse engineering conference in Canada, Ang Cui, founder and CEO of Red Balloon Security, is scheduled to present a talk titled "Ice Ice Baby: Coppin' RAM With DIY Cryo-Mechanical Robot."
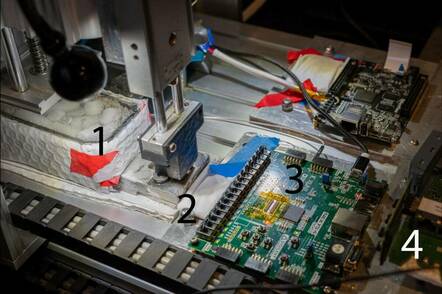
The presentation focuses on a Cryo-Mechanical RAM Content Extraction Robot that Cui and colleagues Grant Skipper and Yuanzhe Wu developed to collect decrypted data from DDR3 memory modules. The rationale for doing so is that hardware manufacturers have made it more difficult to reverse engineer their devices – by disabling JTAG debugging interfaces and UART circuitry, and through using ball grid array (BGA) packaging and encrypted firmware.
"We're seeing what I call product finishing, where manufacturers are removing a lot of debugging interfaces," Cui told The Register in an interview. "It doesn't necessarily increase the security of the product, but it does make introspecting the device and reverse engineering the device a whole lot more difficult. It's kind of just wasting time, getting around some of these hardware things.
"So we decided to kind of change that dynamic by going a different route," said Cui. "Instead of trying to do fault injection, which we've done in the past, or do some very invasive reverse engineering by laser ablation, we built this very affordable, surprisingly accurate robot that literally freezes one RAM chip on the device at a time."
"Then we pull the physical memory off of the device when we want to read the content of the physical RAM – we slam it into our little FPGA fixture. It's basically just reading physical memory by grabbing it from the device and then putting it physically into the reader. And it has actually worked surprisingly well," Cui explained.
- You'll never guess what you can do once you steal a laptop, reflash the BIOS, and reboot it
- I got 99 secure devices but a Nintendo Switch ain't one: If you're using Nvidia's Tegra boot ROM I feel bad for you, son
- AMD's SEV tech that protects cloud VMs from rogue servers may as well stand for... Still Extremely Vulnerable
- SK Hynix admits to DRAM defects, smacks down rumour it botched big batches
"A lot of times in the bootloader, you're gonna see decryption keys. You're also going to see the bootloader code – which a lot of times, if you have encrypted firmware on flash, and you have a boot ROM that's secure even somewhat, you can have a really hard time even getting access to read the code. But with this approach, you get the code, you get all the data, you get the stack, you get the heap, you get all the physical memory," he recounted.
The original cold boot attack, Cui said, involved freezing a laptop's memory by inverting a can of compressed air to chill the computer's DRAM. When memory chips can be brought down to around -50°C, the data represented within can be temporarily frozen – so that it persists for several minutes, even when powered down.
"But if you look at embedded devices, they don't have modular RAM," said Cui. "It's all soldered on. We also worked on a number of very custom memory controllers. We used this approach to do the Siemens vulnerability disclosure work earlier this year.
"So once we got one memory chip pulling off reliably and then reading correctly, we had to do not one but five chips, because they're all interlaced together. And then three of the chips are on one side of the board, and two of them are on the bottom of the board. So we had to come up with a way to somehow magically either pull all five memory chips off at literally the same instruction – which is, you know, hilariously complicated and it's just not really doable."
Tricky stuff, timing
"We came up with this other really cool trick where we do this one at a time and we're looking for not just deterministic execution, but we're also looking at the electromagnetic emanation of the device to figure out basically where the device is going through CPU-bound operation periods. Because if you're CPU-bound, guess what you're not doing? You're not writing from memory," he recalled.
"So instead of needing to have like tens of nanoseconds of timing resolution when pulling the memory chip off, we got periods of tens of milliseconds where we can do this. And that was how we pulled off five memory chips at the same time, and then reconstructed memory for the bootloader, the code and the data, and got visibility to the device."
And tens of milliseconds, Cui, said, is long enough for a computer numerical control (CNC) machine – acquired for about $500 from AliExpress and modified – to perform the necessary chip manipulation.
The robot – a CNC machine attached to a memory reader built with a field-programmable gate array (FPGA) and a controller based on an ESP32 module running MicroPython – simplifies the cold boot attack technique, making it less onerous.
Cui said that the robot consists of a CNC that has been stripped of imprecise components, like the motors and X-axis actuator. What makes the attack possible, he said, is something called a conductive elastomer IC test socket.
In contrast to typical test sockets that are shaped like a clamshell and have metal pins, the elastomer test socket has the consistency of hard gummy bears and is printed with conductive pins.
The flexibility of the socket made it possible to have a piston push the memory chips into place with cheap hardware, without damaging the circuit board or memory chips. And these sockets, which cost hundreds of dollars each a decade ago, can now be had for something like $30 on Taobao.
By incorporating an FPGA-based memory readout system, there's no need to gain code execution via a custom bootloader to dump DRAM contents. The robot also simplifies the attack process by physically transferring DRAM chips between the target device and the readout system.
It works, but all is not lost
Cui and colleagues demonstrated their robot on a Siemens SIMATIC S7-1500 PLC, from which they were able to recover the contents of encrypted firmware binaries. They also conducted a similarly successful attack on DDR3 DRAM in a CISCO IP Phone 8800 series to access the runtime ARM TrustZone memory.
They believe their technique is applicable to more sophisticated DDR4 and DDR5 if a more expensive (like, about $10,000) FPGA-based memory readout platform is used – a cost they expect will decline in time.
Cold boot attacks can be countered with physical memory encryption, Cui said.
"In modern sort of CPUs, and also in game consoles, they're actually already using full encrypted memory," Cui explained. "That would defeat this approach, because even if we were able to rip the physical memory, we would still need to have the physical key, which is somewhere else in the device."
"But the more important a thing is for the world, the less security it has," he said. "So guess what has [memory encryption]? XBox has it. PS5 has it. Guess what doesn't? Every PLC [programmable logic controller] CPU on the planet effectively. A lot of the critical infrastructure embedded things that we depend on, almost none of them are addressing this kind of attack." ®