This article is more than 1 year old
MoD contractor hacked, 831 members of defence community exposed
MoD: We've been hacked, just don't talk to The Register about it
Exclusive Up to 831 members of Britain's defence community with high-level security clearances had their personally identifying information stolen when the Ministry of Defence's business networking organisation was hacked, The Register has learned.
Although heavily redacted in places, correspondence between the MoD and Niteworks—requested under the Freedom of Information Act—has revealed how much the British defence community was exposed by the successful cyber-attack on Niteworks which we reported last year.
Niteworks, whose breached website has now been “undergoing maintenance” for over five months, is intended to provide the MoD with a formal networking forum.
A press release preceding the hack announced that Niteworks' contract had been extended by two years to 2018 (with a predicted total value of £155m). Ironically, the release described the the organisation as offering “wide-ranging expert advice in support of armed forces operations and capability planning, including the delivery of effective training through defending against cyber attack”.
Last November, an email sent to Niteworks members confessed that “the database holding the login information for the members' area in the niteworks.net website has been attacked, and several false accounts were set up,” with the MoD saying “no HMG sensitive information has been compromised.”
As required by an MoD Industry Security Notice (PDF) contractors and sub-contractors are obliged to immediately report “any security incident involving MoD owned, processed or generated information (e.g. incursion, security breach, loss or compromise)” to the Joint Security Co-ordination Centre (JSyCC).
This report was included in the redacted emails acquired by The Register, which reveal that while Niteworks itself reported the breach to the ICO, it was unsure “if there was any specific format” that should be used to report the incident to JSyCC, which BAE Systems had informed the organisation that it had to do. One email also noted that “BAE Systems (who host Niteworks but were not responsible for our website) intend to report the high level issues to [JSyCC] separately.”

In its report to JSyCC, Niteworks offered a brief timeline of events and details of the site:
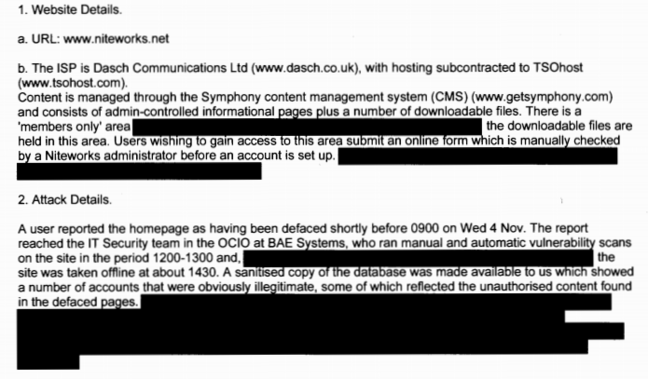
The defacements, described elsewhere as amounting to “advertising for various herbal pills” suggest the target of the breach was not the database that was exposed. Rather it may have been a spammer exploiting a common vulnerability to attempt to flog herbal pills—commonly marketed through spam—though it must be noted that such a spammer had managed to register several fake accounts on the site.
It may also be suspected that a more advanced threat actor may have purposefully chosen to deface the site to conceal their access of what Niteworks described as “the personal data of MoD and defence industrial partner staff which was limited to name, organisation and email address”.
Passwords were also accessed – though Niteworks suggested that they had in fact been encrypted, and not stored in plaintext as we were initially informed and reported. “A password field was also in the database but this was encrypted and there is no evidence that the encryption was defeated,” the company told JSyCC although it is unlikely that evidence that the “encryption was defeated” would be found in the logs of the breach activity.
The MoD declined to inform The Register whether or not it had identified any suspects or who they might be.
Niteworks reported that its website “held files as well as static content”, which the attackers were able to access. A full list of the nature of files is included below, and as the networking folks note, “no information was classified above OFFICIAL”.

Responding to the hack involved basic vulnerability testing, including upgrading the software in its deployment of open-source CMS provider Symphony, and completing an audit of registered users.
On the data breach side, emails “were sent to the 831 non-suspicious account addresses informing them of the breach, advising them to change passwords in any other sites using the same combination of email address and password as was used at niteworks.net, and warning them of the increased likelihood of phishing attacks against their registered email address.”
Of those emails, 355 were “returned as undeliverable, and messages were sent to representatives of the organisations concerned asking for the message to be forwarded to the relevant individuals if possible.”
Elite Hacks
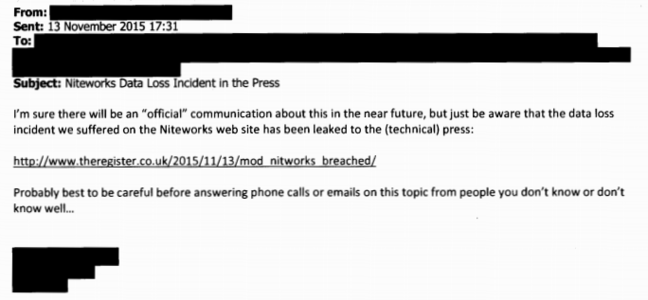
Among the flurry of emails sent in response to the attack, one exchange between Niteworks and the MoD encouraged individuals to be careful before answering phone calls or emails on the topic.
This we would have assumed was standard practice when personal information had been compromised in a hack affecting hundreds of individuals with varying degress of security clearance, however it seems an infamously wiley adversary had provoked such response.
The MoD told The Register that it is “aware of the defacement attack on www.niteworks.net on 4 November 2015. Immediate action was taken and there has been no evidence of any negative consequences of the attack on either members or Niteworks.”
Niteworks had not provided a comment as of publication. ®
