This article is more than 1 year old
It's a cert: Hundreds of big sites still unprepared for starring role in that Chrome 70's show
Bloody SSL...it's the final countdown
Hundreds of high-profile websites are still unprepared for the total disavowal of legacy Symantec-issued digital certificates that will kick in with the release of Chrome 70 next week.
Chrome 70, out on 16 October, will no longer recognise Symantec-issued certificates including legacy-branded Equifax, GeoTrust, RapidSSL, Thawte and VeriSign.
Next week's deadline completes a withdrawal of support that has been ongoing for the last year. Phase one of the process took place in April with the arrival of Chrome 66 and meant that certs issued before the start of June 2016 stopped working for users of the latest and subsequent releases of Google's browser software.
Chrome 70 marks the end of trust for all TLS server certificates issued by Symantec's old infrastructure. The decision to distrust the certs comes after Google Chrome's browser team lost "confidence in the trustworthiness of Symantec's infrastructure" following a series of transgressions against industry best practice.
The disavowal is a community response to alleged violations but Google is on the front line of implementing the shutout.
Scott Helme, the security researcher behind securityheaders.com and report-uri.com, applied scripts to web crawler data to work out which of the web's top million sites are still using Symantec certificates. A total of 1,139 were running them as of 25 September, just three weeks away from the 16 October deadline, Helme's research revealed.
Some affected sites including ferrari.com and postnord.se have changed their certs over recent days so that they are no longer throwing up warnings, but hundreds of others worldwide remain unprepared.
Helme's latest figures are an update on a similar exercise he carried out in April, when he discovered that around 500 of the top million sites were about to stop functioning smoothly in April and 4,971 in October unless they replaced their digital certificate.
Several prominent UK organisations need to change up their certificates before next week. These include Hill and Dale Outdoors (hillanddaleoutdoors.co.uk), Micro Scooters (micro-scooters.co.uk), External Invoicing (externalinvoicing.co.uk), new and used car dealer Marshall (marshall.co.uk) and HomeoVet Animal Care (homeovet.co.uk), among others.
As things stand, surfers using Chrome 70 will be confronted with a big, red warning when they visit these websites next week. Beta users are already seeing warnings that are due to go mainstream in just days. Surfers can just click past such warnings to reach a site but this is hardly behaviour to be encouraged. Any site running Symantec certs will have effectively replaced the welcome mat with the digital equivalent of a "thar be monsters" sign.
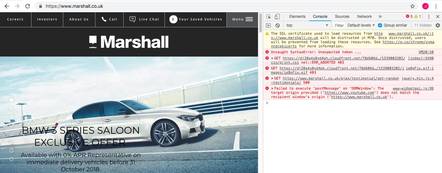
Used car dealer Marshal needs to swap out its Symantec-issued cert for new parts pronto (click to enlarge)
El Reg identified issues in the named sites on Tuesday, 9 October, after going through Helme's latest list.
Readers can verify these results by visiting the relevant sites and looking in the Developer Tools bundled with their Chrome browser. In the console there's an error message confirming these sites will trip up and stop working normally with the release of Chrome 70.
Symantec sold on its digital certificate business to DigiCert last August. Web admins have the option of either moving over to DigiCert or other providers in order to avoid problems. Those not replacing their digital certificate before the imminent deadline risk inadvertently erecting digital barriers to prospective customers.
What should people be doing?
Why are a substantial number of orgs still unprepared for a well-signposted change announced months ago? Helme added that the tweaks were far from difficult to enact.
"This should be a really easy change for organisations to make, especially given how much notice there has been for the upcoming change," he told El Reg. "Replacing a certificate is something that can be done in as little as a few minutes or up to a few days depending on your process and the type of certificate you get. Either way, the worst-case scenario still makes it possible for organisations to change their certificates before the release of M70, despite having already had months of notice."
Tardy organisations have possibly not caught up on the news of the imminent disavowal of Symantec-issued certificates despite a steady volume of coverage about the issue, Helme speculated.
"My guess for why organisations haven't replaced these certificates at this late stage only comes back to them not knowing the change is coming," he said. "There has been a lot of publicity about this change and Chrome has been reaching out to sites that would be affected, along with researchers like myself publishing details and lists of sites that will be affected. I doubt a site would choose to ignore this change and then break in the most popular browser in the world so it surely has to be that they simply don't know." ®

