This article is more than 1 year old
Researcher reveals Chinese e-crime shopping list
Crazy low prices for app 'purchases', or perhaps you'd like a poison PoS unit?
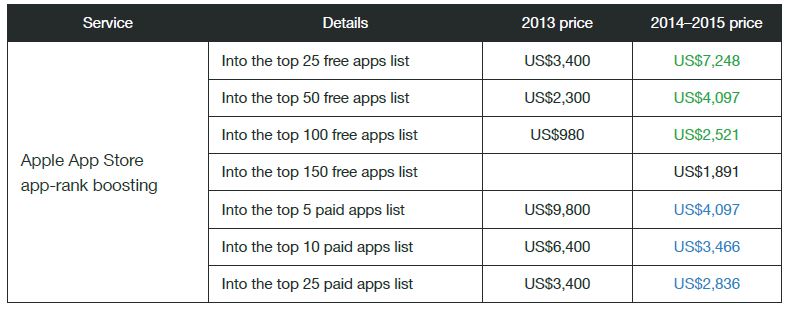
Dodgy developers can have their data-stealing iOS applications boosted to the top ranks of Apple's App Store for as little as US$4000 thanks to services on offer by Chinese hackers.
The price will get an application capable of evading Apple's security checks onto the top five paid application list through boosting services.
A payment of $US7200 will get an app onto the sought-after top 25 free apps lists, a price increase of $3800 since 2013.
By contrast deviant developers can score 10,000 downloads for their malicious Android app a paltry US$16.
The findings are part of analysis of the Chinese criminal underground by Trend Micro forward threat researcher Lion Gu.
He finds in the paper Prototype Nation: Innovations in the Chinese Cybercriminal Underground [PDF] that many of the security crime offerings in Chinese marketplaces will likely be adopted by hackers in other countries.
Gu's price list continues: 80,000 spam iMessages costs $630, corporate email hacking can be done for $95, while a distributed denial of service attack maxing out at 100Mbps from 2000 nodes will cost $79 a month.
The most expensive service he found was cracking encrypted thumb drives which could cost up to $12,600.
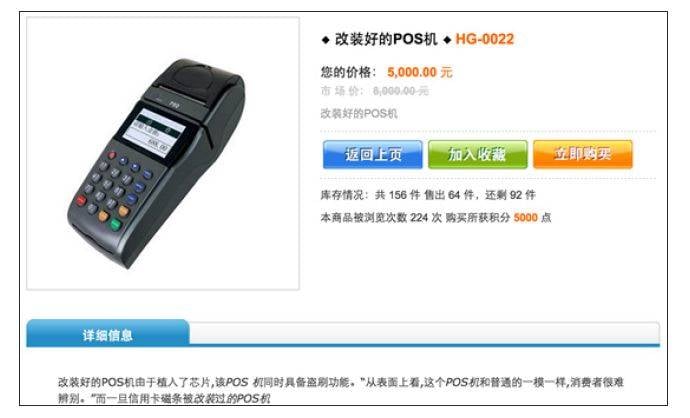
Perhaps the most financially devastating fraud identified in the report is the rise of mass-produced infected point of sales terminals which are being bought by scammers and sold to unwitting Chinese businesses allowing customer credit cards to be shipped off to fraudsters over SMS.
Gu finds modified point of sales terminals are being sold by criminal companies to unwitting wholesalers who then resell the devices to retail stores and chains. Next stop: mass credit card theft.
"These mass produced devices have been introduced into otherwise legitimate business equipment sales and supply chain operations," Gu says in the report.
"Legally operating businesses are selling mass produced, malicious payment card devices to other organisations with neither being aware, ultimately victimising the customers of both.
"Some of the PoS skimmers sold underground even have an SMS-notification feature [which] allows cybercriminals to instantly get their hands on stolen data via SMS every time the tampered devices are used."
At least one infected point of sales fraud campaign netted US$236,500 for a company flogging the devices to restaurants and hotels. Some 1100 credit cards were found on the company's servers.
Mass production has also hit the ATM carding space with panels sold for about $600. Those units are sold on the same sites and contain facilities to steal magnetic stripe data and a camera to record PINs.
The device can be upgraded with a keypad overlay to more effectively steal PINs, if you've another US$300 to spend.
Shop clerks can opt for a $140 pocket skimmer which they can use to swipe customer credit cards when out of sight
Courses in how to card are also on offer selling on Tor hidden services and other forums for about $500.
Gu says the devices are being sold on business to business sites like 1688.com at low cost to attract supply chain businesses.
China is the "birthplace" for broader crime trends, Gu says, with the "most important" innovations occurring in the carding space. ®