This article is more than 1 year old
Apple: Another bug fix. Er, thanks, GCHQ
Things that make you go hmmm...
GCHQ’s CESG (Communications-Electronics Security Group) assurance arm was behind the report of an OS X bug to Apple that the consumer electronics giant patched last week.
The UK’s signals intelligence is perhaps better known in security circles for finding and exploiting software vulnerabilities in order to spy on foreign governments and other targets, but it occasionally discloses flaws through its assurance arm.
Whether this is because the flaws in question have outlived their usefulness and never were much use in the first place is unclear. It’s also possible that the flaw was judged to be a risk to Western government and business and this outweighed its utility as a cyber crowbar.
We just don’t know.
Apple, for one, isn’t looking a gift horse in the mouth, so it decided to patch a memory corruption issue that created a code injection risk by fixing flaws in its IOFireWireFamily technology following notification of the bug or bugs from CESG.
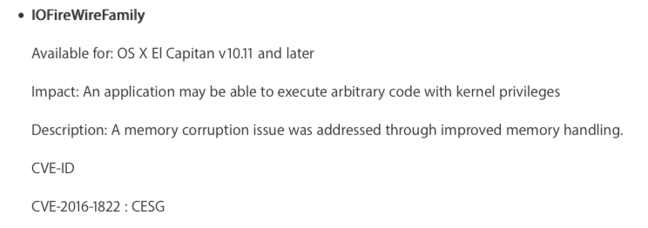
CESG was credited for Apple bug report [Source: Apple security advisory]
GCHQ’s CESG arm is also jointly credited with flagging up memory corruption issues in the Mac OS X kernel that were likewise resolved in this month’s patch batch.
The helping hand from elements of GCHQ is far from unprecedented, even though it’s seldom noted. GCHQ’s CESG arm also reported bugs covered by an Apple update back in March, as we previously noted here.
The significance of the co-operation is difficult to gauge but it goes against the grain of historical spy agency practice. In an intelligence organisation with both offensive and defensive roles - such as GCHQ or its US cousin the NSA - attack will always take precedence over defence, a former US Army intel analyst wisely told us a few years back.
More details on what’s inside OS X El Capitan v10.11.5 and security update 2016-003 for earlier systems can be found in Apple’s advisory here. ®
